What Can Someone Do With Your Email Address? These Are the Dangers
How cautious are you with your email address? Keeping it a secret isn't exactly an option, since it's essential for receiving notifications and facilitating communication – but have you considered the risks if it falls into the wrong hands?
In this guide, we'll let you know what cybercriminals or bad actors can do with your email address, and how to best protect your digital mailbox.
How Your Email Address Can Be Misused
Your email address is an important part of your digital identity, which makes it a popular target for spammers, fraudsters, and cybercriminals. That's why it's good to know how an email address can be misused and what risks are associated with it.
Spam
Annoying, but usually harmless – that's spam. We're talking about unwanted emails, sent in bulk, that typically promote or try to sell something.
How dangerous spam is depends entirely on what its sender wants to achieve. Unwanted ads are tiresome, but they don't pose much of a risk to your digital safety. But even harmless-looking spam emails can sometimes include malicious links or attachments.
How to recognize spam?
Most of the time, a closer look at the sender's address is enough to figure out if it's genuine or not. Long and complicated email addresses like "jvinprax99djv@wxcssaf.zanity.net" are a sure sign of spam.
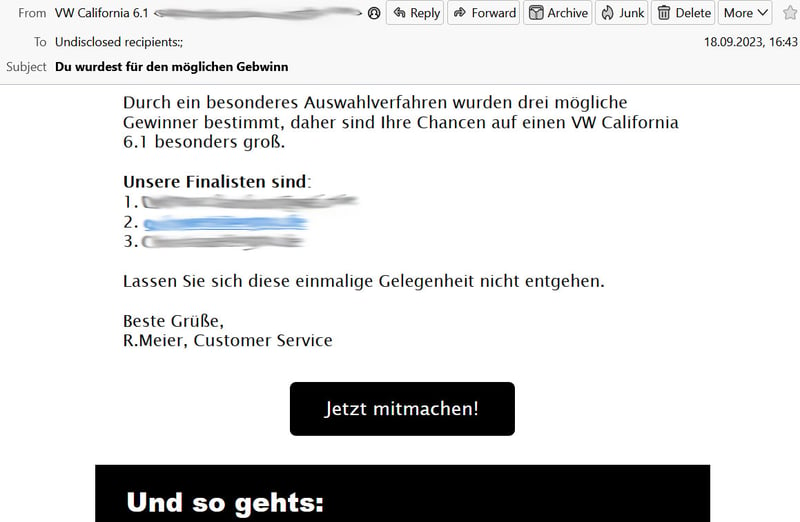
There are many sure signs of a spam email, such as grammatical or spelling mistakes, and unwieldy sender addresses.
Of course, you can also recognize unwanted marketing and spam by its content. You'll likely be prompted to buy, order, or sign up for something. Don't be fooled by bargain prices or special offers, and carefully check whether the email comes from a sender you trust.
Phishing
Phishing is related to spam, but far more dangerous. This tactic, which uses fake emails, is commonly used by scammers to gather personal information. The most common targets include sensitive details, such as usernames, account numbers, or passwords.
How to recognize phishing?
Just like spam, you can often recognize phishing attempts by examining the sender's address. But beware: these fraudsters tend to disguise their email addresses to make them look genuine at first glance (for example, "help@ebay-support.com" – a domain that looks like it's from ebay, but isn't).
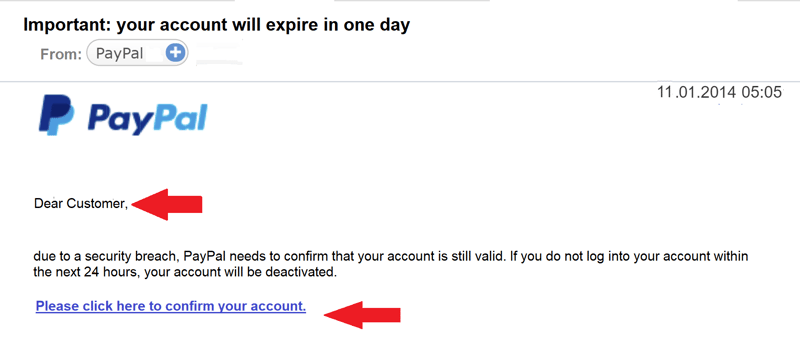
The PayPal logo in this email looks real, but the generic greeting and a closer look at the email address show it to be fake.
Most of the time, you'll be asked to click on a link and input sensitive data, such as your password. If you ever receive an email that asks you to enter a password, especially if certain actions are threatened if you don't (that your account will be deleted, for example), alarm bells should be ringing.
Malware & Viruses
Of course, emails can also be used to infiltrate your devices with malware and viruses, hidden in links or attachments. That's why you shouldn't click on links or open attachments that you haven't verified as coming from a trusted sender.
Brute Force Attacks
Once they have your email address, cybercriminals can launch brute force attacks against any accounts that it's linked to. That's when attackers try all possible combinations in an effort to crack your password.
Other Risks
Unfortunately for their victims, cybercriminals can be quite clever and inventive. That's why the list of potential risks and dangers is long. Here are a few others you should keep in mind:
Doxing
When someone publishes personal information about you without your permission, that's called doxing. Should cybercriminals gain access to your email account, they can tarnish your reputation, release private correspondence/media, or even publish sensitive information like your number or home address. This is often intended to emotionally damage or bully the victim.Selling of data
Many data brokers gather email addresses to sell them to third parties. Once they're in circulation, they can be misused for any of the above threats, from spam campaigns to phishing attacks or identity theft.Identity theft
Some fraudsters don't just spam indiscriminately, but attempt to trick you in a very targeted manner. To do this, they 'steal' the identity of people you trust – such as family members or acquaintances – and use this facade to lure you into their trap.
How Can I Protect Myself Against These Threats?
As you can see, scammers and spammers might use your address for quite a few unwanted and potentially harmful activities. The good news is that an email address alone isn't enough to cause any serious damage.
As long as you don't fall for the scams, you have little to worry about. To ensure this, you should follow some rules:
Basic Online Safety Measures
Before resorting to software solutions, there are a number of general measures you can take in your daily digital lifes:
Check the sender of emails
Always look at the sender's address of emails – especially if it is an unexpected email, if it contains links or attachments, or if it asks for personal information or payment details. While scammers often use the name of a legitimate organization, a closer look at the email address often reveals inconsistencies.Don't click on email links
Are you unsure whether an email really comes from the stated sender (e.g., your bank)? In that case, instead of following the link in the email, simply open the website manually in your browser and log in there to find out whether the message/request is legitimate.Pay attention to encryption
If you have followed a link or opened a website directly in the browser, you should make sure that the connection is encrypted. You can recognize this by the "https" abbreviation and the lock symbol next to the address bar of your browser.Be cautious with personal information
Don't disclose sensitive data (e.g., passwords or bank details) in emails. Reputable providers won't ask you for such information in the first place. Also, be cautious with other personal information unless you are 100% sure of the recipient.Use multiple email addresses
It can make sense to create several email addresses instead of just one. Set up different email addresses for certain types of activity (e.g., one for online shopping and another for social media). This makes it easier to identify phishing emails.Education & awareness
Stay informed about the latest phishing schemes and cyber threats to be aware of what sort of digital dangers there are.Don't create accounts everywhere
With every user account you create, the circle of companies that know your email address grows. Even though companies must follow strict rules when handling email addresses, it can always happen that they fall into the wrong hands (e.g., through leaks). It can't harm to be selective about where you create an online account.
Use Strong Passwords
Simple passwords are a gift to hackers. Therefore, the best protection against the aforementioned brute force attacks are strong passwords.
Every password you use should be long (at least 8 characters, 12-16 are even better) and contain letters, numbers, and special characters. You should avoid obvious, easily guessed information, such as birthdays or names of family members.
Furthermore, you should use a unique password for each account you use. If you use the same combination of email address and password for numerous services, a hacker only needs to be correct once to gain access to all of these services.
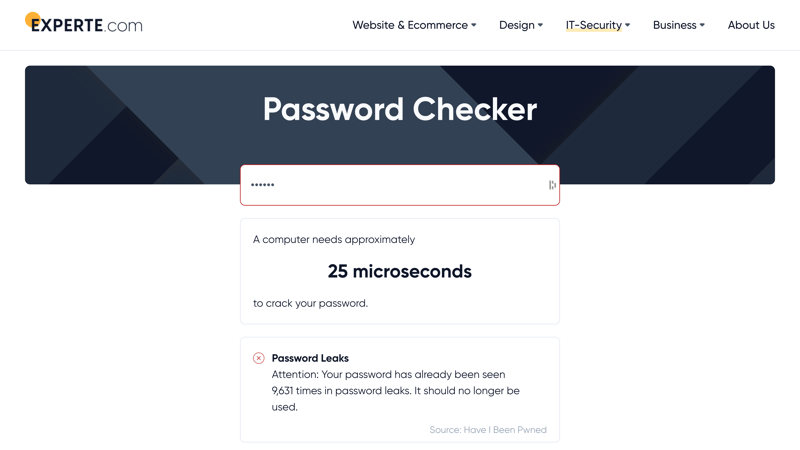
Use our password checker to see how safe your passwords are.
The more accounts you have, the harder it is to manually create and remember a powerful, unique password for each.
That's where a good password manager comes in. It stores your passwords and other sensitive information and supplies it automatically when you need it. All you have to do to unlock your vault is to remember a single, strong master password.
To help you select the best tool for your needs, we've tested 12 of the most popular password manager out there. You can find our detailed reviews, as well as many other guides on the topic, here:
Two-Factor Authentication
Two-factor authentication (2FA) is a security mechanism that enhances the protection of your accounts by adding an additional verification layer to the login process.
This means that when you log into your user account, you won't just be asked for your password, but you must also enter a second code or confirm the login through a second factor, often on a different device. As a result, stealing your password is not sufficient for hackers and data thieves, because they lack the second factor.
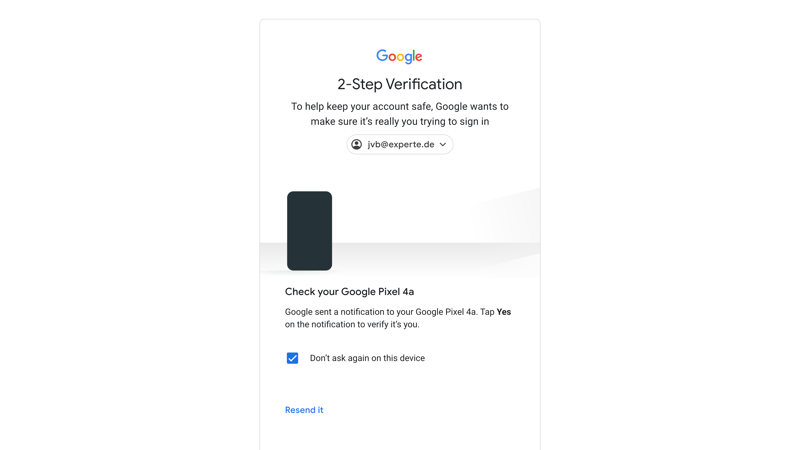
With two-factor authentication enabled, your account remains safe even if someone manages to crack your password.
Most online services, especially those that handle sensitive data, offer 2FA, usually with a range of settings and options.
You'd prefer not to confirm your identity with a second factor every time you want to log in somewhere? In that case, make sure to at least set it up for the first time you access the service from a new device.
Antivirus Programs
When it comes to more advanced threats that you might not have been able to mitigate through preventative measures and cautious online behavior, antivirus programs can help. They scan, identify, and remove malware from your devices and actively protect them against viruses, trojans, ransomware, and other malware.
In addition, most antivirus suites now also come with parental controls that help you limit online dangers for your children, as well as theft protection features that can help mitigate damage in case of theft.
We have tested some of the most popular antivirus programs and reveal how reliable their protection is:
How Do Strangers Get My Email Address?
You might wonder how strangers get a hold of your email address in the first place. The list of potential sources and methods is long:
Data leaks and theft
There are occasional data leaks at companies or online services where customer data, such as email addresses, is stolen. You can use an email leak checker, such as haveibeenpwned.com, to see if your email address has been leaked in the past.Carelessness
If you share your email address on social media, in public forums, or comment sections, you have no control over who ultimately sees it – and what they do with it.Sign-ups and registrations
Even though there are strict laws and regulations about sharing email addresses with third parties, some online services might do so nonetheless. You may have even agreed to this data sharing in the fine print.Guessing
Simple or "logical" email addresses like "firstname.lastname@gmail.com" or "info@company.com" are, of course, easy to guess.Address book hacks
When someone whose address book contains your email address falls victim to an attack, your data could be compromised.Scraping tools
There are specialized software programs that systematically search the web for email addresses. These programs can automatically comb through thousands of pages in no time, extracting any email addresses they find.
Conclusion
Your email address is an important part of your digital identity, which makes it valuable to fraudsters, hackers, and other cybercriminals. Fortunately, just knowing your email address alone doesn't allow third parties to cause real damage. However, it can serve as a starting point for targeted attacks or spam.
Therefore, you should always check the sender of emails you receive, be careful with links and attachments, and protect all of your digital accounts (including email) with unique and strong passwords, ideally stored in a password manager.
You're looking for a secure email provider? Be sure to check out our list of the safest email services.
Frequently Asked Questions
You can use an email leak checker, such as haveibeenpwned.com, to see if your email address has been leaked in the past, and if so, by which services.
Someone can use your email address to send you spam, phishing emails, or malware. If you use a weak password, you could also fall victim to a brute-force attack. In addition, there are risks such as identity theft, data sales, or doxing, which is the disclosure of your personal information.
You can often recognize phishing and fraudulent emails just by taking a closer look. Often, they have unusual sender addresses or the emails themselves are full of spelling and grammar errors. Frequently, you'll be asked to enter personal data or follow suspicious links. When in doubt, you should contact the respective company directly or open its website in your browser.

















