Data theft has become an epidemic, impacting not only multinational corporations but also regular people. Cybercriminals exploit technical ignorance, naivety, and human emotions with damages forecast to amount to trillions of dollars - per year - by 2025.
Below, we'll let you know what dangers are lurking and how you can effectively and proactively guard against data theft.
What Is Data Theft?
Data theft is the illegal acquisition of personal, secret, or sensitive data, whether from companies, organizations, or individuals. Over the past few decades, cybercriminals have grown more sophisticated and daring. The methods listed below are some of those most commonly used:
Corporate/organizational data leaks
Data leaks happen when highly sensitive data is released against the will of those who store it. This sort of theft can occur digitally or via physical media, such as USB sticks, and often includes customer or user information that is sold by (disgruntled) employees.Phishing
With phishing, cybercriminals impersonate bank employees, police officers, or customer support, contacting unsuspecting victims via phone, email, or text messages. Once they've gained their trust, they request that payments be made to specific bank accounts or solicit personal details, such as passwords and PINs either over the phone or on fake websites that look like the real deal.Keylogging
One of the most dangerous threats lurking online is keylogging, which records every keystroke a victim makes. In this way, passwords, login credentials, or even corporate secrets can become readily known.Malware
Malware is an umbrella term for malicious software that intentionally damages the computers it infects. It can turn up nearly anywhere, and there is no silver bullet to preventing it from finding its way onto your system. Viruses, adware, spyware, and Trojans are just some of the subtypes of malware that can cause significant damage.
What Are the Consequences of Data Theft?
Data theft can take a number of different forms. Sometimes victims remain completely oblivious to the fact that they've been targeted, while on other occasions, the consequences are drastic and unmistakable.
Identity Theft
Identity theft occurs when a criminal impersonates someone else, using that "identity" to engage in illegal activity, like hacking a social media account. There are a number of different types of identity theft:
Cybercriminals use fake profiles to spread lies and misinformation about their victims. Those they are impersonating will have to contend with damage to their reputation as well as legal and financial impacts.
When criminals gain access to an account and assume their victim's identity, they can misuse their personal data to open new accounts on online shopping platforms and place huge orders. With banking information, they can apply for new credit cards, take out loans, or sign up for services, financially ruining their victims.
Another repercussion of identity theft that shouldn't be underestimated is spam emails. Whenever an email account is hacked, criminals can send messages in the name of their victims. Alternatively, you might receive emails that look like spam, but are actually genuine and relate to fines or punishment for non-compliance that have arisen owing to the identity thieves' activities.
Doxing
Doxing (sometimes also written as Doxxing) has been around since the 1980s and started out as a relatively harmless form of pranking someone. Today, it has lost most of its innocence, with modern-day doxing relying on publicly available information that is released to hurt its targets. Whether intimidating, intended to blackmail, or simply making them appear stupid, doxing is anything but fun.
Extortion
When it comes to making a fast buck, extortion is one of the oldest tricks in the book. However, in the digital domain, thanks to ransomware, the process has become both more sophisticated and random. This type of malware encrypts individual files or even entire systems, demanding a pay-off for the decryption code. Such fraud causes billions of dollars in damages every year.
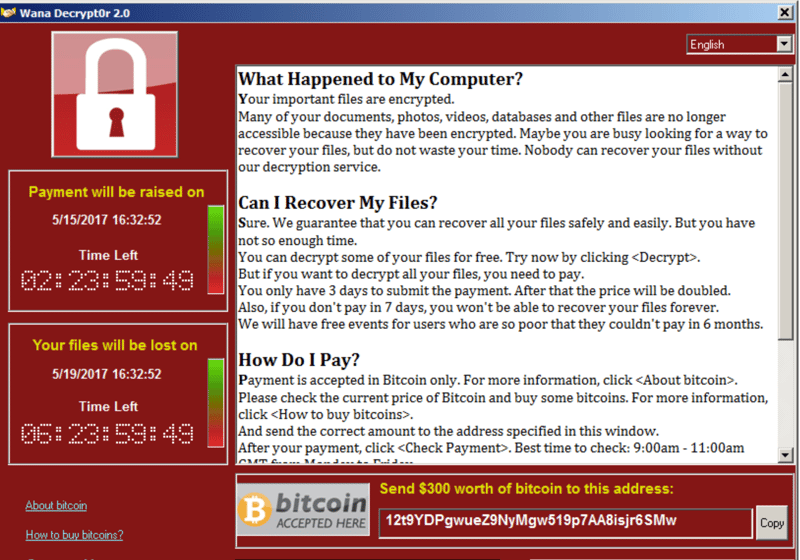
If a message like this appears on your PC or laptop, you've been infected with ransomware.
How to Find Out if Your Data Has Been Stolen?
Data theft isn't easy to recognize, and even when it is, you might not have missed the warning signs. For example, since spam emails are mostly ignored, genuine warnings or notices from legal or debt-collecting firms that might be legitimate are written off. As such, we recommend taking any of the below warning signs seriously:
Pay attention to any unsuccessful login attempts for your email accounts, social media profiles, or elsewhere.
Don't ignore warning emails sent by service providers you have accounts with, such as eBay, PayPal, or Amazon. At the same time, be sure that these are authentic emails and not phishing attempts.
If your computer or laptop starts behaving oddly after installing a new piece of software or visiting a strange website, scan it immediately using anti-virus and anti-malware software.
In the event that your password suddenly stops working, it may have been cracked and changed without your knowledge.
Regularly check your activity log. Should any unfamiliar or unrecognizable transactions appear, this can be a clear sign that the integrity of your account has been compromised.
If invoices, bills, fines, or letters from debt collectors begin to regularly appear, chances are that your identity has been stolen. Someone is likely using your data to order goods and then have them delivered to a different address.
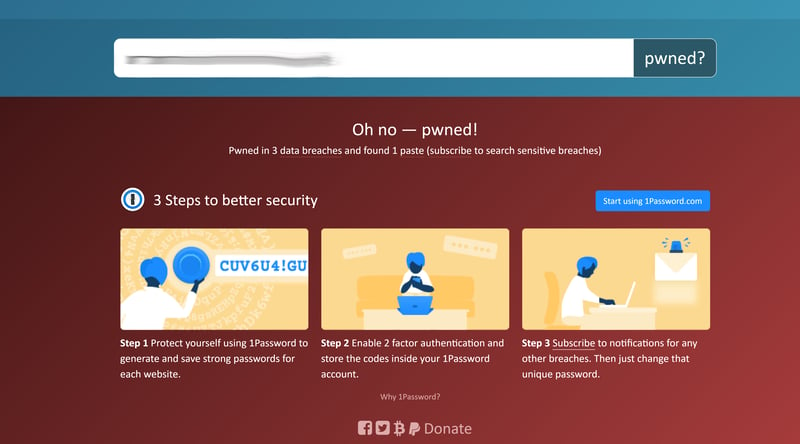
Services like Have I Been Pwned? make it easy to to find out if your email address has been leaked.
One way to enhance your digital security is to check whether your email address has been leaked. There are several free services that you can use to do this:
On Have I Been Pwned? you can see whether your email address or telephone number has been released in any data leaks. The provider also offers a very long list of Internet sites where hackers upload illegally acquired login credentials.
Pwned Passwords serves as a useful supplement to Have I Been Pwned? allowing anyone to determine whether their passwords have been compromised. These passwords are included in the so-called "dictionaries" that are used in brute force attacks.
Firefox Monitor uses data from Have I Been Pwned? but with a neat twist. After registering via email, you'll receive regular updates whenever your data pops up across the web.
Identity Leak Checker assesses whether, based on your email address, any of your personal data, such as your birthday, telephone number, or physical address, have been released.
After inputting your email address, F‑Secure ID PROTECTION tells you whether your data has been stolen in an email that includes all of its findings. You can also register with F-Secure to test all of the service's features for free for five days.
How to Protect Against Data Theft?
Victims rarely realize that their data has been stolen until months or years later. For that reason, we recommend taking a more proactive approach when it comes to your digital security. The steps below will help to avoid nasty digital surprises:
Strengthen your passwords
Avoid combinations like 123456 or hello123 and use at least 8 upper and lowercase letters, special characters, and numbers in your passwords. Create a unique password for each account you have too. You don't have to remember all of these uncrackable passwords either, so long as you're willing to use a password manager. We comprehensively tested several of the leading solutions.Install antivirus software
Every computer, tablet, and smartphone should have antivirus software installed. Antivirus software protects against malware that can seriously damage any system. We tested the best antivirus solutions on the market, and you can check out our findings in our comprehensive evaluation.Be careful with emails
Take care when opening emails, even from people you know. You can never be 100% sure that someone hasn't had their email account hacked. Also, never click on links in emails that look odd, as these can contain malware. Never open or download email attachments without verifying their content with the sender.Use public WiFi with caution
Everyone loves free WiFi, however, the moment you connect to a network, your device becomes visible to cybercriminals and can be easily hacked. One of the best ways to protect against this is by using a VPN, which encrypts your data traffic, making your device invisible to would-be attackers. Be sure to check out our review of the best VPNs on the market.Update your operating system
Whenever an update is available for your operating system, particularly a security patch, we recommend downloading and installing it. The same is true for all programs or apps you have installed but in particular your antivirus or malware protection suites. Keeping software up to date closes gaps or exploits.Safely browse the Internet
Even the best tools, services, and features only offer a baseline of protection. The most important steps any Internet user can take are to exercise caution, a healthy amount of skepticism, and common sense. Trust no one who appears to be after sensitive or personal data, and never provide too much information on social media platforms like Facebook or Instagram.
What to Do if You've Been the Victim of Data Theft?
There's no such thing as 100% protection against data theft. Even if you follow all of our advice, there's still a chance that a digital fraudster can access your data. Your first reaction will likely be anger, fear, or panic. This is understandable, but it can paralyze your response. Instead, take a deep breath and relax, since you'll have a lot to do and likely, very little time to do it. These should be your next steps:
Change your passwords and email addresses
If your email account has been hacked, a new password won't be enough. Smart hackers begin by changing their victim's password, making it impossible to regain access in the short term. The safest thing to do in this scenario is to create a new email address. After that, log in to your most important accounts (online banking, online shopping, social media, etc.) and change the linked email address and password.File a criminal report
Just because data theft occurs online doesn't make it any less of a crime. Once you've secured things digitally, head over to the nearest police station and file a criminal report. Some online services require a scan of this report to lock your account. In this way, you'll also be able to protect against most damages, such as bills or invoices, that a hacker's activities can result in.Inform your friends and family
Get in touch with your family, friends, and acquaintances and tell them that you've been the victim of data theft. If your email account has been hacked, make sure that anyone on your address list knows that they should delete any emails they might receive from you.Inform your creditors and bank
It's a good idea to get in touch with your credit card provider and bank to let them know that someone has stolen your personal data. These will then have a record should loans or charges begin to appear in your name, for example, under a new account or on a new card. They can also lock your accounts or suspend new activity. We recommend monitoring your credit score and contacting your credit reporting agency.Consult specialists and/or a lawyer
Lawyers are paid to represent and protect their clients, and that goes for digital damages as well as physical ones. As an alternative, you can reach out to data theft specialists who will be able to provide you with an immediate plan of action.Dispute charges
Dispute any and all charges you have not personally made. The criminal report you filed earlier will play an important role here since it will show that you didn't have control over your account when the charges were made.
Conclusion
Anyone can fall victim to data theft, even those who don't use the Internet. Cybercriminals have grown more aggressive and creative in targeting their prey, and there's no 100% foolproof solution to ward them off. With that said, there is quite a bit that you can do to reduce the likelihood of being targeted. Should you have already become a victim, reacting quickly is the best course of action.
EXPERTE.com features plenty of reviews for programs that can help you to use the Internet more securely, such as VPNs, password managers, and antivirus software. Still, the best defense against data theft is a healthy dose of common sense: Don't open suspicious emails or click on links to websites, and never use passwords for more than one account.
FAQs
This depends on what is happening: If your bank account is being emptied, call them and request that they lock your account. Should your email have been compromised, create a new account and link all of your digital services to it. If you don't know what to do, get in touch with the police and file a criminal report. After that, seek out a professional, like a lawyer specializing in cybercrime.
Pay attention to any suspicious activity, such as unusual withdrawals or bills for goods or services that you never purchased or ordered. You can also make use of free tools like Have I Been Pwned? to check whether your email address or other personal data has been compromised in a leak.
One of the easiest steps you can take is to use strong passwords and a password manager. Antivirus software and VPNs also go far in helping to minimize exposure and limit digital damage. The most important thing is to not open suspicious emails, click on links within them, or visit dubious websites.
Identity theft is when personal data is misused by a third party for criminal purposes. Most of the time, this is outright fraud, with the thief trying to enrich themselves as quickly as possible at the victim's expense. In other cases, the criminal may harbor a vendetta against their target and want to personally harm their reputation or standing.
Yes: the Computer Fraud and Abuse Act (CFAA) has been amended to cover most forms of digital fraud and identity theft discussed in this article. A first conviction carries a prison sentence of 1-5 years, while a second conviction is expanded to 10 years.











