You turn on your computer, but it doesn't load normally: Your system has been hacked! However, ransomware isn't the only digital danger lurking on the web for both individuals and businesses alike. DDoS attacks and data theft are just as serious and a daily problem for many.
Understanding what you're up against is one of the best ways to effectively counter these threats. In this article, we'll fill you in on the three most common types of cyber attacks and how you can defend against them.
Distributed Denial of Service Attack (DDoS)
DDoS attacks paralyze networks or servers by overwhelming them with requests. These take advantage of the client-server model, upon which most Internet applications operate. Whenever you type the URL of a website into your browser (for example, www.nytimes.com) your computer or device (the client), sends a request to the server that the website is hosted on.
Web servers can answer several thousand requests per second, however, they are limited in terms of bandwidth and even hardware. The more requests that are submitted, the longer the response time, similar to telephone (landline) switchboards of the past. In the worst case, traffic simply collapses and users receive an error message (503 - Service Unavailable) when attempting to visit the site in question.
Those orchestrating DDoS attacks use multiple computers or Internet of Things (IoT) devices to send large numbers of requests at the same time. Strung together, these form a so-called botnet. Most of the time, these devices are infected with viruses or malware and spread across the globe, with their owners having no idea that their computers are being used to hurt others.
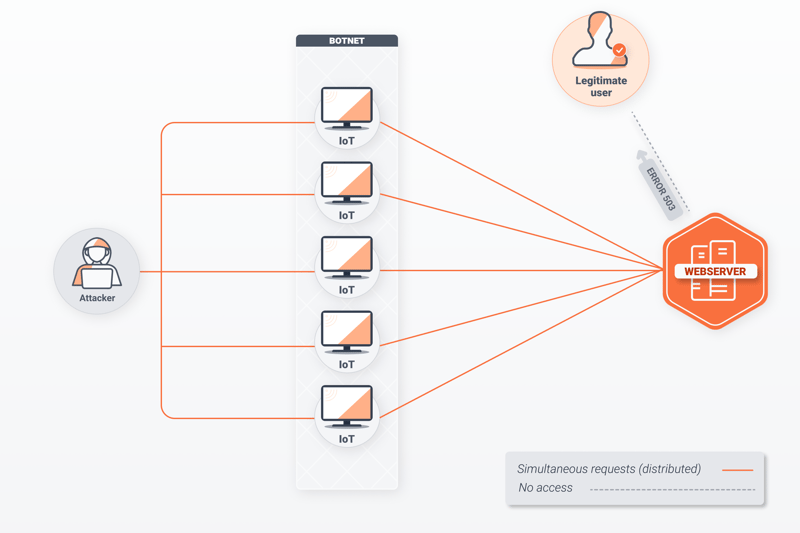
Types of DDoS Attacks
Even though all DDoS attacks attempt to deny service, they go about achieving this in different ways and by exploiting various parts of a network connection. Multi-vector attacks use multiple entry points to attack at the same time.
- 1.
Volume-based attacks target available bandwidth and include user datagram protocol (UDP) floods. During these, bots overwhelm UDP ports with data packets, causing the server to crash. Along with transmission control protocol (TCP), UDP is one of the most-used transport-level protocols. DNS floods function similarly, bombarding the DNS server with requests.
- 2.
Application attacks are launched on the application level (the highest in the OSI model). This is responsible for regulating how integrations interact with users. So-called Slowloris attacks send incomplete requests, rapidly increasing the number of open connections and preventing the server from responding to legitimate queries. Apache web servers are a particularly popular target for such attacks.
- 3.
Protocol attacks take advantage of IP weaknesses. SYN flood attacks spoof the 3-way handshake of a TCP protocol. With TCP protocols, a SYN message is sent to the server, which responds with ACK, followed by SYN-ACK confirmation from the client. If the SYN message contains an incorrect IP address, the server will continue to wait for an answer, until the server stops functioning.
How to Recognize a DDoS Attack?
When a website takes longer than usual to load, you shouldn't automatically assume that it is experiencing a DDoS attack, since peaks in usage can also produce a similar effect. With that said, there are some sure symptoms of a DDoS attack:
Too many requests are received from the same IP address or location;
Unpredictable traffic spikes;
A ping request, which tests a host's availability within a network, returns a "Timeout" error message for the server in question;
When attempting to access the website, a 503 error message appears.
How to Prevent DDoS Attacks?
It isn't possible to prevent DDoS attacks since the infected devices that launch them are unable to be controlled. As such, countering DDoS attacks is all about enhancing network resilience.
- 1.
To counter volume attacks, routers using the anycast methodology will distribute queries to different servers. Most of the time, these are cloud security services that filter out malicious queries, forwarding only legitimate ones. Good providers have powerful networks with traffic of 60 terabytes per second (Tbps), far exceeding the capabilities of botnets.
- 2.
For protocol attacks, service providers offer a number of different programs that analyze user behavior, thwarting bots with captchas. These require the input of letter and number combinations unreadable by computers or the selection of all pictures containing a particular item or object.
- 3.
Web application firewalls (WAF) offer a shield between clients and servers, helping to thwart application attacks. These operate like a doorman, preventing those who seem suspicious from entering.
- 4.
With rate limiting, servers only allow a specific number of requests within a given period of time. Should a low SYN, UDP, or Drop limit be set, the server will reject all packets which exceed it.
The Most Infamous DDoS Attacks
According to Netscout's 2020 Global Threat Intelligence Report, more than 10 million DDoS attacks were launched. Some of the more infamous DDoS attacks of all time include:
In September 2017 Chinese bots sent millions of data packets to multiple Google servers. The UDP flood attack was measured at 2.5 Tbps, making it the largest DDoS attack. Despite its size, its consequences remain unknown.
In February 2020, Amazon Web Services (AWS) reported a three-day 2.3 Tbps DDoS attack. This multi-vector attack exploited a weakness in the connectionless lightweight directory access protocol (CLDAP), the industrial standard for accessing indices. AWS customers were not impacted.
In October 2016, Mirai, a notorious botnet, attacked servers belonging to Dyn, a DNS provider. Since Dyn translates URLs into IP addresses, platforms such as Twitter, GitHub, Reddit, and Netflix were temporarily unavailable. In the aftermath of the attack, Mirai published the code that was exploited for the attack.
Ransomware
Ransomware allows cybercriminals to hack IT systems, encrypting data that is stored on drives. In order to regain access to them, the extortionists demand a ransom. Similar to DDoS attacks, ransomware also frequently targets services, utilities, and healthcare systems.
The most common vehicles for ransomware are phishing emails and attachments infected with trojans, while IT networks with inadequate security are a particularly easy target. Victims include individuals as well as businesses and even government officials.
Just like DDoS attacks, those who engage in ransomware are often hackers from countries like China, Iran, Russia, or North Korea, which makes it difficult or impossible to prosecute them. Since victims often need to pay in cryptocurrencies, like Bitcoin, tracing the recipient is difficult.
Types of Ransomware Attacks
In addition to the well-known CryptoLocker variant, screen lockers are also common. Victims of the latter need to pay a ransom in order to regain access to their screen or monitor. In most cases, cyber extortionists also threaten to release sensitive data if they aren't paid.
How to Recognize a Ransomware Attack?
You'll usually know fairly quickly if your system has been infected with ransomware. Most of the time, a message will display stating that you have been attacked, and providing information about how to proceed. Other symptoms of a ransomware attack include:
The inability to access certain files that were accessible in the past;
Files suddenly appear without an extension, or have the .crypto extension;
Text files (ending in .txt) with suspicious names like "_Decrypt your files" or "_Open me".
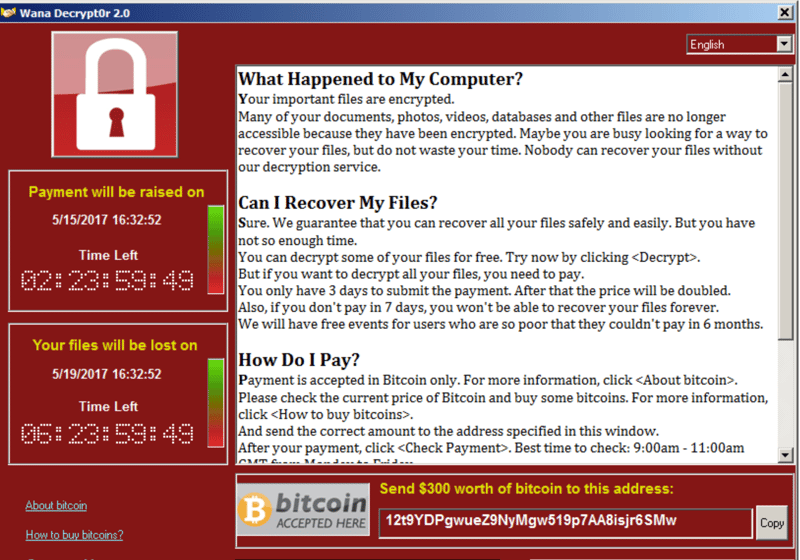
A ransomware attack often manifests similarly to the above.
WARNING! The US Government and all of its cybersecurity branches strongly discourage paying cyber ransoms. There are a few reasons for this: First, there's no guarantee that you will receive the password. Second, by doing so, you provide the cybercriminals with an incentive to continue their activities. The FBI, for example, recommends immediately contacting their local field office if you think you've been the victim of a ransomware attack.
How to Prevent a Ransomware Attack?
Should you already practice good IT security behavior, you're well protected against ransomware attacks. Some aspects to keep in mind include:
Regularly backing up sensitive data. Since ransomware targets backup folders, it's recommended to encrypt your files and store them offline, on external storage devices.
Keep software up to date, since older versions can have weaknesses or exploits.
Uninstall unnecessary plugins and deactivate macros.
Make it necessary for all scripts and active content to be confirmed by double-clicking.
If possible, do not install your browser locally at work, but use a terminal server with a remote desktop connection.
Rarely grant write access for network drives, and even then, only with strong passwords.
Allow remote access only with secure VPN connections and two-factor authentication.
Use firewalls with IP filtering as well as whitelisting services. The latter are lists that include reliable and allowed IP addresses, protecting the server.
Offer workshops on cybersecurity. During these, employees can learn how to recognize suspicious and dangerous emails and websites.
The Most Infamous Ransomware Attacks
According to the FBI, since 2016, more than 4,000 ransomware attacks have been recorded per day. Among the most infamous are:
In March 2019, a ransomware attack paralyzed Norsk Hydro's IT systems, causing production to be run manually for weeks. The company did not pay the ransom and was able to retrieve the affected information thanks to backups.
The largest meat producer in the world, JBS, paid a ransom of $11 million in May 2021 to regain access to its IT systems. The Russian hacker group REvil claimed responsibility for the attack.
Also in May 2021, gas supply to the East Coast of the US was disrupted after Colonial Pipeline Company's IT systems were compromised by ransomware, using an unprotected VPN access point. The company paid the $4.4 million ransom, however, the FBI was able to recover most of the Bitcoins later.
Data Theft
Even though most people speak about data theft, in reality, cybercriminals copy digital information. Most of the time, their goal is to use email accounts for illegal activity, gain access to funds or sensitive information, or tarnish someone's reputation. When it comes to identity theft, the purpose is often to engage in illegal activity while pretending to be someone else.
Data thieves typically identify their victims through phishing emails, inadequately secured networks, or infected websites. For companies, disgruntled employees or those without technical know-how are often responsible when sharing sensitive data without authorization.
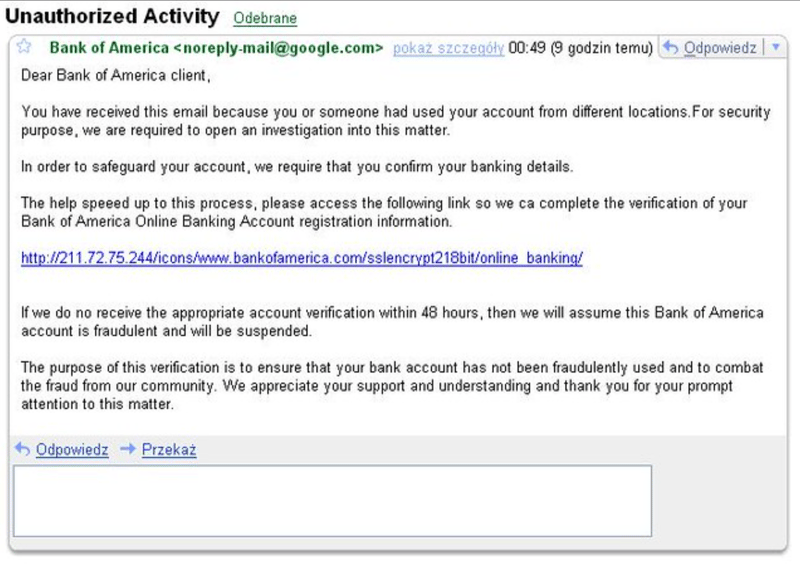
Take a close look: Phishing emails often look legitimate, however, upon detailed inspection, often have an odd feature (or two).
How to Identify Data Theft?
Should criminals gain access to bank accounts, it won't take long for you to notice suspicious transactions. In other cases, hackers will release stolen information online in order to harm the victim. If the information isn't immediately actionable, it can take years for someone to learn that their data was stolen, for example, when applying for a loan or credit card or receiving official mail or court summons.
How to Prevent Data Theft?
As is the case with the other two kinds of cyber attacks, criminals exploit weaknesses in IT systems. Below are some guidelines to help in protecting yourself and your data:
Create strong passwords consisting of numbers, upper and lowercase letters, as well as special characters. Change these at least every six months.
Make sure that your firewalls and antivirus software are up to date.
Store data on external drives, such as a USB stick, encrypt it and protect it with a strong password.
Delete accounts for those who have left the company or organization. Only grant limited access to organizational networks to non-employees or customers.
Offer employee training on phishing, malicious websites, and social engineering. The last of these is a method by which hackers exploit information on social networks to target and probe their victims, encouraging them to provide sensitive details like passwords.
The Most Infamous Cases of Data Theft
In contrast to DDoS and ransomware attacks, leaks of sensitive information pre-date the Internet. The main difference is the scale, with data theft in the 21st century impacting millions of people worldwide every year. Some of the most notorious cases of data theft over the past few years include:
In March 2020, hackers gained access to the servers of CAM4, a video chat platform, making off with more than 10 billion files. These include real names as well as chat and payment logs, making it possible for victims to be blackmailed for years.
In March 2018, cybercriminals hacked the IT systems of one of the world's largest biometric databanks. Aadhaar, managed by the Indian government, stores biometric data including fingerprints, photos, and iris scans for more than one billion Indian citizens.
In November 2018, Marriott International announced that unauthorized individuals had accessed the credit card data of 500 million of its customers. The attack occurred in 2014 but wasn't noticed until 2018.
Conclusion
DDoS attacks, ransomware, and data theft can all compromise your digital security. Fortunately, you can defend yourself with powerful antivirus software, firewalls, strong passwords (that can be easily and safely managed with a password manager), and by regularly updating your software and drivers. IP filters and cloud services help against DDoS attacks, preventing bots from being able to send requests to your site.
Be careful when opening suspicious emails or websites since these often serve as gateways for malware and trojans. If you think that you're the victim of a cyberattack, the best thing to do is to contact local or federal authorities.











