Do you have the feeling that your smartphone is being monitored or that it's been hacked? If so, there are several easy ways to find out if your suspicions are correct. Unfortunately, unauthorized access can go completely unnoticed and background apps can run without your knowledge.
Below, we'll let you know how to identify whether your smartphone has been hacked, what to do if it has, and how to protect yourself against future attacks.
Phone Hacking: What Is It?
Phone hacking occurs when someone remotely accesses a smartphone without the owner's approval or knowledge. Typically, they're after sensitive data, interested in monitoring the phone's owner, or misusing the device.
After hacking a smartphone, criminals have a number of options: They can GPS locate the device, monitor all of its user's communications and surfing behavior, and access stored data. In some cases, they can even use the phone remotely, to activate its camera and microphone, or send messages.
While there is an overlap between hacking and surveillance, the two are separate from one another. For example, parents can use legitimate apps to monitor their children's smartphones or track lost devices.
On the other hand, hacking is an activity that's designed to gain unauthorized access to another device, whether it's a computer, network, server, or smartphone. Surveillance and monitoring can occur after a device has been hacked, but they're not the same.
In addition to data theft and installing viruses on systems, there are also (white hat) hackers who use their skills to identify security weaknesses and exploits in technical infrastructure in order to enhance their defenses.
Hacking Methods
There are plenty of ways that malicious software can find its way onto a mobile end device. Among the most common used by criminals to exploit smartphones are:
Unsafe WiFi networks
Free WiFi is practically everywhere these days. However, these connections usually lack adequate encryption, allowing hackers to exploit their weaknesses and gain access to other end devices. In this way, they'll be able to monitor a user's data traffic or install malware on their device.Malicious links
Tapping or clicking on a link can install malware on your smartphone without your knowledge.Untrustworthy downloads and apps
Unofficial downloads and apps have been known to help hackers gain access to smartphones. Especially with free apps, always carefully read through reviews and when possible, download programs only from official app stores and marketplaces.Phishing
Phishing occurs when users open and click on malicious links or download attachments in an email, text, or social media message that looks like it was sent by someone they either know or trust. Once opened or clicked, malware is installed on the device, or the user is asked to input data into a website that they believe to be genuine, such as for online banking.SIM swap
Also known as SIM hijacking, this hacking method is favored by identity thieves. The goal is to use the victim's phone number to gain access to their social media accounts or online banking.To do this, the criminal needs quite a bit of information (telephone number, name, address, etc.), however, once they have it, they can (officially) order a new SIM card from the victim's provider. Perpetrators usually acquire this data through phishing.
Once the criminal has the SIM card, the victim loses control over their number, with all calls and texts routed to the criminal.
Most of the time, the boundaries between hacking methods are fluid. Unfortunately, cybercriminals are innovative and creative when it comes to finding new ways to prey on their victims and utilize technology to their evil ends.
Have You Been Hacked? These Are the Signs
There are several clear indicators that your smartphone has been hacked, such as an abnormally high monthly bill or loss of control over your number. Most of the time, the changes are more subtle and pertain to how your device behaves.
Changes in Your Phone's Performance
If your smartphone starts to behave differently than normal, such as having significantly less battery life or being slower, it might be infected by malware. Overheating or performance issues (apps unexpectedly quit, your screen freezes, etc.) can also indicate that a background app is overtaxing your phone's operating system.
High data usage
Mobile data usage is relatively consistent for most smartphone users. Should you suddenly notice that your monthly data has doubled or tripled, while your routine has remained the same, chances are good that someone has either accessed your data or that an unwanted app is running in the background.
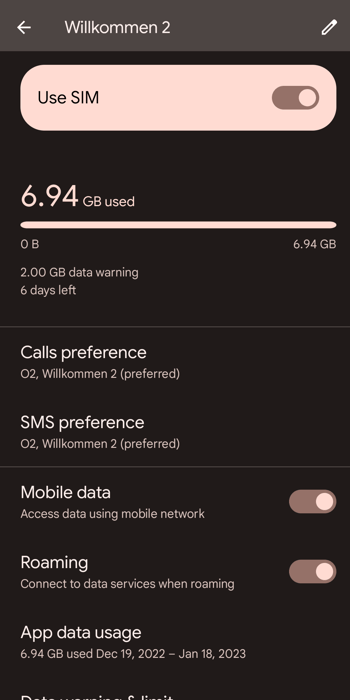
Always keep tabs on your monthly data usage.
Unknown Apps on Your Smartphone
Apps that you can't remember installing shouldn't be on your smartphone. Of course, these aren't necessarily spyware or malware, however, they can be a good indicator that your device has been hacked.
Unknown apps
Surveillance is just one of the many dangers posed by unknown apps: They can also help third parties misuse your phone, utilize its resources as part of a bot network, and/or send spam and malware to your contact list. The problem is, not every unknown app is malicious, however, you should regularly review each program that is installed on your mobile device and get rid of those that you don't know or use.
Spyware apps
Spyware is specifically designed to provide hackers and other third parties with covert access to devices and the ability to manipulate their features, such as cameras and microphones. These programs are freely available from official app stores and marketed as parental control, geolocation, or spy apps.
Unusual Activity
Strange activities during regular use are another indicator that someone has gained access to your mobile device.
Flash, camera quality
If your camera's flash suddenly goes off or your picture quality becomes worse, it's a good indicator that someone has gained unauthorized access to it. Another tell-tale sign is the appearance of images and videos that you don't remember taking.
Strange activities
Outgoing messages or calls that you didn't send or make are a sure sign that your device has been hacked. Strange social media or email account activity, such as multiple login attempts or password changes, require swift and decisive responses.
How to Check Whether Your Smartphone Has Been Hacked
In order to determine whether malware is on your smartphone, start by checking your app list for unknown programs and deleting them. Even though they run in the background, malicious apps aren't invisible.
Find unknown apps
Next, go to your phone's settings menu and look for the Apps area or menu. Pay close attention to those apps that you don't remember installing, those that use large amounts of data, and apps with names like "spy", "monitor", or "stealth".
Since many malicious apps don't actively advertise what they are, it's a good idea to carefully review any unknown or unverified apps. We recommend typing each unknown app's name into Google and checking the results to see whether it's a system file or not.
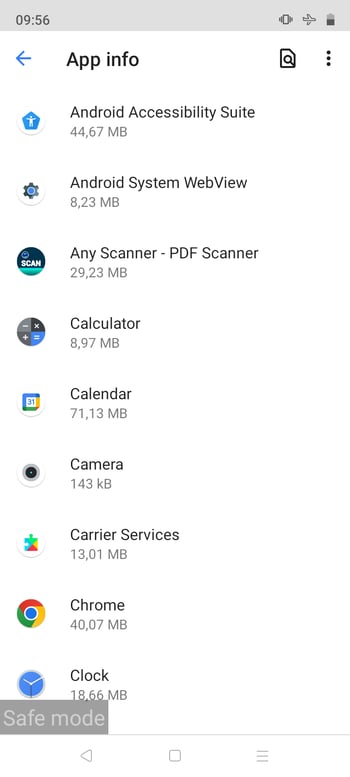
Check that no spyware or unwanted apps have been installed on your phone.
Check administrator rights/privileges
Next, take a look at whether any administrator or root rights or privileges have been granted, especially if your device is used. If you find apps like SuperSu, KingRoot, or BusyBox, delete them. When unsure, you can use special checking apps to determine whether your smartphone has been hacked.
Hack check apps
There are special apps that automatically check your phone for unknown and malicious apps. These are marketed under a variety of different names (such as antivirus, anti-malware, spyware remover, etc.) and are capable of finding and neutralizing the most dangerous smartphone malware.
Was Your Smartphone Hacked? Do This Now!
If your worst fears have been confirmed and your phone was hacked, every second counts. In most cases, you'll be able to permanently remove the malware from your device by following these steps:
Isolate Your Smartphone
Isolate your phone by removing your SIM card and disconnecting from any WiFi connections. This prevents installed malware from sending or receiving data.
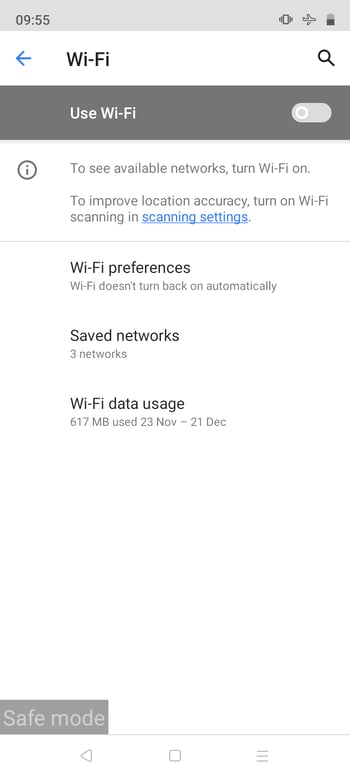
Start by quarantining your phone.
Go Into Safe Mode
In case you didn't do it when removing your SIM card, power down your phone and restart it in safe mode (press the volume down button until the start animation is finished). This prevents all third-party apps from loading, limiting your phone to the necessary, factory-installed apps.
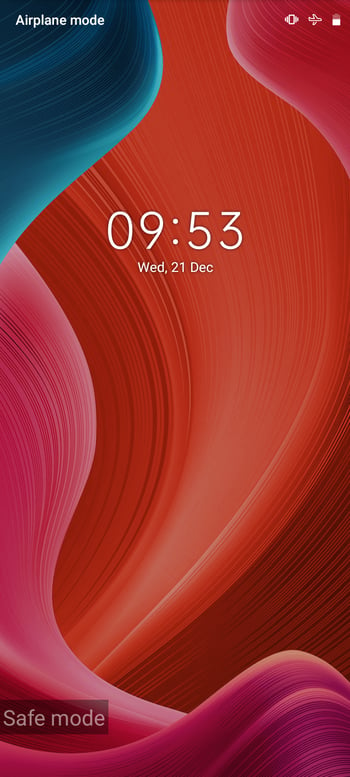
Restart your phone in safe mode.
Delete Malware and Suspicious Apps
Once your device has restarted in safe mode, go to the Apps area of the settings menu and delete any programs that you don't recognize or have doubts about.
Restart Your Phone
Any malware that was on your phone should now be deleted. Still, since it isn't always easy to completely remove these, and they're notoriously effective at camouflaging themselves, we recommend erring on the side of caution and resetting your phone to its factory settings.
How To Protect Your Phone?
As the saying goes, "An ounce of prevention is the best cure", and that also applies to phone hacking. Security precautions, just like on your desktop or laptop, are just as important and effective at protecting your smartphone against threats. Smartphone manufacturers are keenly aware of the dangers posed by spyware and malware and do offer solutions to help ward off attacks.
Beyond that, there also exist a number of reputable third-party apps that can be used to guard your smartphone.
What Solutions Do Smartphone Manufacturers Offer?
iOS
Apple's multiple defense levels make it easy for iPhone users to protect their devices against malware. The entire operating system (and all apps) run in a secure environment which effectively prevents communication with external apps. Overall, iOS is an extremely safe operating system, so long as it's updated to the most current version.
Samsung Knox
Samsung Knox is the Korean tech giant's proprietary security platform for its smartphones. Secured by Knox offers additional real-time protection against malware and other threats and is available on most Samsung devices.
Which Apps Protect Against Hacking?
There are many different ways to protect your smartphone against hackers. Some apps promise to guard against malicious programs, while others identify and help remove existing malware from your device.
Antivirus
Just like on a desktop or laptop, mobile antivirus apps scan your phone's storage for dangerous or damaging content. Once complete, you'll be shown a list of all suspicious files and be able to remove them.
Most antivirus apps provide real-time protection, constantly monitoring your device's system for threats and alerting you before they can cause any damage. For more information about which options are available for Android devices, be sure to check our antivirus test.
Spyware remover
Spyware removers or anti-spyware apps are specifically designed to identify and neutralize spyware. Like antivirus apps, they scan your device (its apps and processes) in real-time, alerting you to dangers like unauthorized camera access.
VPN
A virtual private network encrypts your Internet connection and prevents third parties from spying on your activities. With these, you'll be able to surf much more safely on public WiFi networks.
NordVPN won EXPERTE.com's VPN test.
What Else Can I Do To Protect Myself?
To start, it's a good idea to never leave your smartphone unattended or to allow strangers to use it. This effectively prevents others from physically accessing your device. In order to head off Internet threats, also keep the following in mind:
Password Protection and 2-Factor Authentication
Strong passwords exponentially enhance any device's security. Be sure to use a unique password for every account and device. Keeping track of these is easy with password managers.
Another step you can take is to activate 2-factor authentication. Important accounts, like those for your email or online banking, should always be secured with multiple security factors (such as a password and a separate one-time code sent via text or through an authenticator).
Software and app updates
Don't procrastinate when it comes to software updates! These prevent known security exploits from being used to hack your smartphone. When your operating system and apps are up to date, your susceptibility to external threats is dramatically reduced.
Block third parties
With a third-party blocker, you can prevent hackers from making calls or sending messages using your phone. You'll need to activate this with your phone provider, however, it stops third parties from making charges to your account.
Pay attention to the installation source
By only downloading programs from official app stores, you minimize the likelihood that you'll accidentally install malicious software. On Android devices, you can automatically block installations from unknown sources through the settings menu.
Exercise caution when using Bluetooth or WiFi
Enabling Bluetooth allows anyone nearby to connect to your device, without your knowledge. For that reason, be sure to disable Bluetooth whenever you're not using it. The same goes for public WiFi: Only connect to password-protected networks and even then, be sure to use a VPN.
Research unknown apps
It's a good idea to regularly check the apps that are installed on your smartphone and remove any that look suspicious. With the help of an antivirus app, you can make sure that malicious software is automatically identified before it has a chance to wreak havoc on your system.
Conclusion
Do you have the feeling that your smartphone has been hacked? If so, remove your SIM card, disconnect from WiFi, and take a look through your device's app list for unfamiliar programs.
Since surveillance apps and malware are often hidden behind harmless-sounding names, you might want to consider using an antivirus app to sniff out and neutralize any dangerous programs. These offer solid protection against new threats as well and should be standard on every smartphone.
Beyond that, there are a number of other preventive measures you can take, such as regularly updating your device's software, using a VPN, creating secure passwords with a password manager, or blocking third parties.
FAQs
Typical indicators that a smartphone has been hacked include a sudden loss of performance, unexpectedly high data usage, or unusual activity without any logical reason. The appearance of unknown apps can also signal a successful hacking attack.
If you suspect that your smartphone has been hacked, time is of the essence. Disconnect your device from WiFi, remove the SIM card, and look for suspicious apps. Antivirus apps can help you find and remove these.
Antivirus apps help to effectively defend smartphones against hackers. Using a VPN further increases your security, especially when surfing on public WiFi.
Yes, so long as it is your smartphone or that of your underage child. Unauthorized monitoring of any phone belonging to a third party is considered wire fraud and a felony punishable by hefty fines and/or prison sentences.












