Phishing is a problem wherever people work. According to Proofpoint, three-quarters of all businesses experience a phishing attack of one kind or another. And they're becoming more sophisticated as well, with infected pages looking more like the real deal every day. In this article, we'll let you know how you can identify phishing attempts and protect your data.
What Is Phishing?
Phishing refers to the sending of professional, genuine-looking emails which request sensitive data from their recipients, either directly, or upon visiting an infected site. Most of the time, phishers are after online banking PINs or passwords, so that they can drain accounts. Phishing emails can forward their victims to infected websites or even be used to launch ransomware attacks that install malware and render your computer useless.
Phishers often try to pass themselves off as employees of reputable businesses or organizations, despite not having any affiliation with them whatsoever. Most commonly, they'll send emails that look like they came from the bank, business, or social network and threaten users with suspending their account unless they login within 24 hours.
Many phishers disguise themselves as PayPal staffers.
Phishing is a kind of social engineering since cybercriminals don't have to take advantage of technical weaknesses (code errors or exploits), but rather, human emotions and fears. After gaining their victims' trust, they can easily con them out of their data.
The URLs found in phishing emails often look just like those of trusted and reputable websites. Since the page's layout doesn't have any clear differences from the real thing, no alarm bells are set off. In addition to website spoofing, there's also domain spoofing, whereby a reputable email address is displayed in the message's header. It's not uncommon for both types of spoofing to be used side-by-side.
The term's origins are not entirely clear. One theory is that it's 'fishing' but spelled using 'leetspeak', an Internet language. In this, words are spelled by substituting phonetically identical sounds with one another or swapping numbers with letters (or vice versa). Alternatively, some argue that the spelling is derived from "phone phreaking", a type of 90s telephone hacking that reversed tones to allow free international calling.
Whatever its roots, one of the first recorded usages of the term was in 1996 when mentioned in conjunction with AOHell, a piece of malware that stole AOL usernames and passwords.
What Types of Phishing Are There?
All phishing attacks pursue the same goals: Gain their victims' trust and steal their sensitive data. With that said, the type of attacks varies depending on the target group:
Classic phishing – Basic phishing emails are bulk sent to random addresses. The senders impersonate workers at popular platforms or businesses like PayPal, Amazon, or Facebook. This makes it more likely that targets will volunteer information without the sender needing to invest any time or effort in scouting them. Recipients are often asked to change or confirm their password owing to an alleged security breach.
Spear phishing – As its name suggests, unlike classic phishing, spear phishing targets a specific person. This is usually, an executive, IT administrator, or IT manager within an organization. Phishers who do this often attempt to pass themselves off as working for IT companies that market products used by the victim's organization.
Whaling – This type of phishing goes after the big fish, that is to say, CEOs, managers, or departmental heads. These leaders receive emails that look to be from within the company or from trusted business partners. To appear as legitimate as possible, hackers will research their targets online, checking their social network profiles, copying older pictures, and even reading through comments.
Around 94% of all phishing attacks occur via email, however, there are two other varieties of phishing attacks:
Smishing (SMS-Phishing) – Attackers send their victim an SMS. Like classic phishing, a link redirects the victim to an infected website or starts a malware download.
Vishing (Voice Phishing) – This type of fraud impersonates police officers, bank employees, or IT staffers, who proceed to request sensitive data from their victims.
How Can I Recognize a Phishing Email?
Unfortunately, it isn't possible to always discern a phishing email from a legitimate one at first glance. This is because most phishers create authentic-looking logos, layouts, and even signatures. In the event that you receive an email that you think is fraudulent, do not click on any of its hyperlinks or supply any data. Pay attention to the following signs:
Emails from organizations with non-specific domains
Companies and authorities never use commercial email domains like @gmail.com or @yahoo.com. Businesses, such as banks, will only ever use the bank's domain, while for government or state authorities, the email address should originate from a .gov domain. For that reason, pay close attention to the domain. Delete all emails that don't have a clear sender.Generic greeting
Legitimate queries always refer to a customer or individual by name or username. Generic greetings like "Dear Sir/Madam", "To whom it may concern", or "Hey!" usually signify some sort of fraud. If you're uncertain about the legitimacy of an email, you can always contact the company or organization directly (ideally through another channel or their verified customer support) before passing judgment on the original message.Grammar and spelling mistakes
Professional businesses the world over have high standards when it comes to syntax, spelling, and writing. Still, it is possible for a legitimate email to be missing a word or have a typo. All the same, if the message has an error in every sentence, or just doesn't 'sound' right, alarm bells should ring. In the event that you notice multiple grammatical or spelling errors in an email, we recommend deleting it.Payment requests via email
In some cases, cybercriminals pretend to be debt collectors or legal firms, threatening their victims with sizable fines if they don't pay up within a given time period. Legitimate legal firms will only ever get in touch via mail. Here too, it's a good idea to delete any such emails immediately.Emails with attachments
Banks and insurance providers generally do not send any data to their clients in the form of attachments. Instead, after logging in to your bank or insurance account, you'll be able to download any required files directly from the platform. Keep an eye out for .ZIP, .EXE or .RAR attachments, and do not download, execute, or unzip them.Different URLs
If you receive a suspicious email containing a hyperlink, hover your mouse over the link for a few seconds. After this, you should see the actual URL that the link leads to. Should the text and link not match, it's almost certainly an infected website. Close untrusted websites immediately, and delete any email which prompted you to visit them.PIN and/or password request through a link
The most distressing phishing attacks are online banking scams. Most of the time, victims get an email with a link to a website that looks fairly similar to that of their bank. If a victim logs in, the hackers gain access to their account.Banks will never ask customers to log in to online banking via a link. Any email asking you to do so should be ignored and deleted.
Notorious Phishing Attacks
Phishing attacks are nearly as old as the Internet itself. Over the past few years, however, hackers have conned quite a few highly lucrative victims. Some of the most infamous of these include:
The Loveletter computer worm has caused around $10 billion worth of damages since May 2000. A Filipino IT student forwarded an email that had a subject line reading "ILOVEYOU". Anyone who clicked on the attachment which the email contained unknowingly installed malware on their computer which would delete large numbers of files. Loveletter was the first case of phishing that generated global attention.
Between 2013 and 2015, a Lithuanian scammer sent fake invoices in the name of Quanta to workers at Facebook and Google. Prior to being caught, he earned around $100 million.
Crelan, a Belgian bank, lost more than €70 million in a spear-phishing attack in 2016. Hackers impersonated CEOs and managed to convince the bank's finance department to transfer funds to a variety of accounts.
In 2015, a spear-phishing attack managed to knock out the three largest Ukrainian power suppliers after compromising their IT infrastructure and SCADA systems. In the aftermath, more than 200,000 people lost electricity for more than six hours.
What Should Victims of Phishing Attacks Do?
Should you have become the latest victim of a phishing email, your focus should be on minimizing damage:
Immediately change all passwords for any impacted accounts (i.e. Amazon). If you do this fast enough, there's a good chance that you won't suffer any consequences. Over the following days, keep an eye on any suspicious account activity or failed logins.
Should you no longer be able to log in, this means that hackers have already changed your password. Contact the company (ideally, by telephone), lock your account, and cancel any pending orders.
If your bank account has been compromised, immediately lock your online banking and inform the bank's staff. Report the matter to the police as well.
Should you have incurred any financial damages, get in touch with a lawyer specialized in cyber criminality.
Prevent Phishing: How to Protect Your Data
Never click on suspicious or dubious links. If you do click on a link, make sure that it's to a secure website (in most browsers, a green lock icon will be visible to the left of the URL).
Serious applications, like those for online banking, don't open in pop-up windows. For that reason, never input sensitive data into a pop-up window, and make sure you're using a pop-up blocker.
Check your email provider's spam filter. Keep in mind that even the best filters won't block all phishing emails.
Password managers only input a password when the URL you open matches what's on record. As such, these provide considerable protection against website spoofing.
Configure emails to display in text rather than HTML. This reduces the likelihood of inadvertently clicking on a malicious link. It will prevent images in legitimate emails from displaying correctly, which could be inconvenient.
Regularly update your antivirus software.
Create frequent backups of your data. In this way, you'll limit any potential damage caused in the aftermath of an attack.
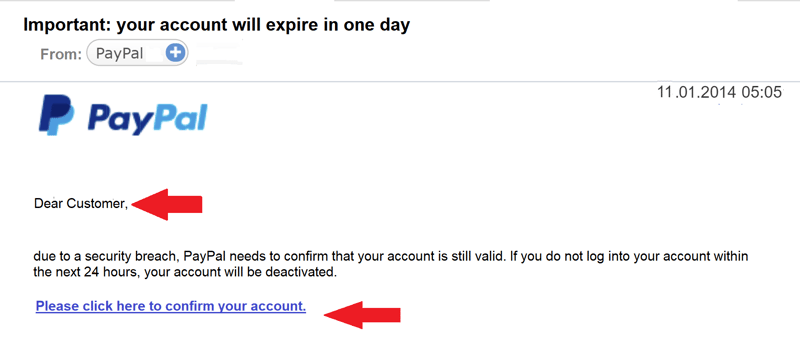
In the above email, the PayPal logo looks authentic, however, the greeting and non-matching email addresses show that it's a phishing email.
Conclusion
Phishing attacks happen very often. Digital conmen try to convince victims that they are reputable to access their sensitive data. Be alert whenever you get an email asking for your password. You can reduce your exposure by only clicking on trusted links, regularly updating your antivirus software, and only opening email attachments after you've checked with the sender. If you've fallen prey to a phishing attack, IT specialists and legal experts can help.
FAQs
Phishing emails can be hard to identify. Spend a minute or two reading through the email and look for a generic greeting ("Dear user"), poorly written copy, and links that go to a URL different than what's written. Generally, any email containing an attachment from someone you don't recognize, or from a public email domain (rather than that of an organization or company) is highly suspect.
If you still have access to the affected account, log in and immediately change your password. Should this not be possible, contact the platform or company directly and lock your account. In the event of financial damages, contact a lawyer and report the incident to the authorities.
Spam filters like those used by most email services offer decent protection against phishing emails, while antivirus programs and anti-malware software recognize malicious attachments and links. Password managers provide yet another line of defense against phishing, since they only supply login credentials when the URL matches the one on record.











