Every 11 seconds someone suffers from a ransomware attack. Cybercrime Magazine's 2019 prophecy has come horribly true, and the Internet now appears more dangerous than ever. Losses from ransomware attacks exceed billions of US dollars per year, making it the most profitable form of malware in history.
While this is great news for cybercriminals, ransomware is as dangerous for everyone else as bank robbers or bandits once were. But don't fret, we'll show you how to protect yourself in this guide.
What Is Ransomware?
Ransomware is a widespread form of malware, known alternatively as an extortion Trojan. These programs take specific files, or your entire system hostage (through encryption), and demand a ransom in exchange for their release, through a decryption key.
The first ransomware attacks happened in the 1980s when programs were smuggled onto systems via floppy disks. Since then, ransomware attacks have grown more sophisticated and common, causing billions of dollars in damages every year. But how does ransomware work?
Encrypt documents
Files on your system are encrypted against your will. This is why ransomware is sometimes referred to as a crypto or extortion Trojan. On occasion, ransomware will completely lock you out of your system or device. This is referred to as locker ransomware.Demand a ransom
Once your files or system are encrypted, the hostage-taker demands payment for their release. Only then will they send a decryption key which you can use to unlock your files. Payment is usually requested in cryptocurrency like Bitcoin. Should you refuse to negotiate or pay, your files will likely be deleted. Most ransomware displays a countdown until deletion, encouraging you to pay up.Even if your payoff is received, there's no guarantee that you'll receive a decryption key. For that reason, many, including the FBI, strongly advise against paying.
Ransomware is no joke, but what makes it such a threat?
WannaCry
One of the most infamous ransomware attacks ever happened in 2017 using the so-called WannaCry software. This used a Windows exploit that the NSA took advantage of for surveillance and intelligence-gathering. In the wake of the WannaCry outbreak, 230,000 devices around the world were locked.
Owing to the resulting breakdown in their IT infrastructure, the British National Health Service (NHS) had to face 92 million GBP in damages, as well as large numbers of canceled appointments and operations.
It doesn't matter if you're a private individual, a company, or even a governmental organization or ministry: No one is safe from ransomware attacks. But how do these programs get onto computers in the first place?
How Does Ransomware Infiltrate My System?
Like most malware, ransomware is often hidden in corrupted files or executable programs. There are several ways ransomware can infiltrate your computer:
Security flaws in operating systems and software
Software developers constantly close security gaps through patches and updates. If unresolved, hackers can use these to infiltrate your computer. Ignoring updates, or using outdated (unsupported) software can be an invitation for trouble. WannaCry preyed upon the outdated, Windows XP systems of the NHS.Email attachments
Like other malware, ransomware likes to piggyback on emails, either directly in attachments or infected links.Corrupted Internet sites
Entire websites can be elaborate ransomware traps. As soon as you visit one, a drive-by download begins which secretly loads the program onto your computer.
How Can I Protect Against Ransomware?
Regardless of how ransomware gets on your system, once it's there, it can unleash considerable damage at any time. Like most things in life, the best protection against ransomware is to be proactive. There is specialized software, but sensible browsing behavior and responsible computer usage are two of the best ways to avoid ransomware.
Regularly update your operating system & software
Because the NHS's digital infrastructure used Windows XP, its computers were easy targets for WannaCry. Once security flaws become known, they're patched with updates. At the same time, this also signals to malware developers that they can exploit those same weaknesses on non-updated systems. For things like your Internet browser, pay regular attention to updates.As long as your operating system and commonly used programs are kept up to date, the risk of falling victim to a ransomware attack significantly decreases.
Back up your files often
If a ransomware attack "only" encrypts your files, you'll need to consider how important the encrypted files are. Should they be saved elsewhere, temporarily losing them can be more of an annoyance than a catastrophe. The best way to remove ransomware is to reinstall Windows on your computer. For that reason, we recommend regularly backing up your data with a dedicated cloud service.Be careful when opening email attachments
Like most malware, ransomware can be hidden in email hyperlinks and attachments. We recommend only opening attachments after you've confirmed who the sender is. Infected emails often look like legitimate messages from businesses like Amazon, Paypal, or Apple with convincing subject lines. Upon closer inspection of the sender, however, it becomes clear that these messages are not official.Use antivirus software with ransomware protection
Installing security software which includes ransomware protection is certainly the safest option. Nearly every antivirus suite includes this feature nowadays, however, most reserve them for paying subscribers. As part of EXPERTE.com's comprehensive assessment of 15 of the leading antivirus solutions, we paid close attention to these features. You can view the results in our anti-ransomware evaluation.
How Do I Remove Ransomware?
And what to do when prevention is off the table? One thing is certain: Ransomware doesn't stay hidden for long, since the entire purpose of the software is to generate money. As such, if a few days or weeks have passed since opening a questionable email attachment, or clicking on a strange pop-up, your system is most likely not infected.
As another "benefit", ransomware extortionists are relatively polite, as far as cybercriminals go. If you've been infected, you'll probably see a message like this:
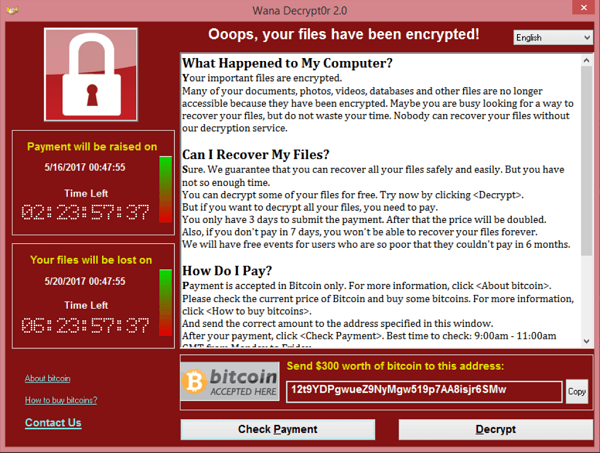
Internet hostage takers are relatively polite, but they can cause considerable damage.
There are many solutions depending on the strain of ransomware you've been infected with, and which resources are at your disposal. Here, we'll show you how to remove ransomware.
Conclusion
There are good reasons for the fear and hysteria about ransomware: Every year, this dangerous kind of malware wreaks financial havoc that amounts to billions of dollars. If these attacks were only directed against governments or large corporations, it would be one thing, but they aren't and impact regular people too. As soon as the software is on your system, your options become extremely limited.
For that reason, prevention and being proactive are the best defenses. If you don't open any suspicious emails, visit questionable sites, and regularly update your software and operating system, you become much less vulnerable. To improve your chances even more, the anti-ransomware features included with antivirus programs can round out your digital defenses.











