Privacy and anonymity are only important if you have something to hide, or? Every Internet user should decide which parts of their lives are private and which are made public. While reasonable, ISPs, corporations, and cyber criminals all have an insatiable hunger for one thing - your data.
In this guide, we'll let you know why it's important to safeguard your privacy online and which methods you have for surfing more anonymously.
What Traces Do You Leave Online?
Criminals aren't the only ones on the lookout for your information: Third parties, like Internet service providers (ISPs) or owners of websites you visit, can learn quite a bit about your behavior through your IP address, making it easier to identify you. They won't find your name, but they can see your physical location and which websites you visit and search for.
Beyond that, everyone who uses the Internet is exposed to some degree of tracking: This occurs when third parties monitor your online activities using what are known as cookies. Most of the time, there's nothing sinister about this, with the focus instead on optimizing websites and increasing profits through personalized advertising.
Finally, there are also criminals who try to gather valuable data and information about you, for launching more sophisticated cyber-attacks. Whether monitoring you on public WiFi or visiting non-encrypted websites (those without HTTPS SSL certificates, easily recognizable by their closed lock symbol in the address bar), these villains can sneak a peek over your digital shoulder.
With the EXPERTE.com Privacy Check you can see what your digital footprint is like.
Surfing anonymously isn't about hiding anything, but rather, keeping your data private and away from third parties. There are a few good ways to do this.
Step: Conceal Your IP Address
Think of your IP address as the number on the door of your home or apartment. It can offer some clues as to who you are. In the worst case, cybercriminals can use your IP address to uncover your identity or access one of your devices.
There's good news though, as several ways exist to hide your IP address. Below, we've listed some of the most popular:
Proxy Server
A proxy server acts as an intermediary between you and the Internet, replacing your IP address with its own. This means that you never come into direct contact with the websites you visit, and they won't be able to see your location. One neat benefit is that you can bypass country or region blocking, making it possible to access otherwise unavailable content on Netflix & Co.
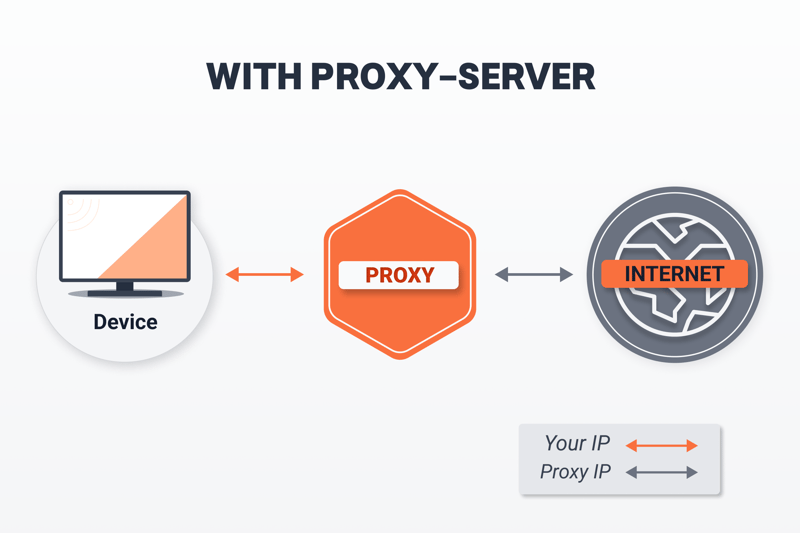
Proxy servers operate between your device and the Internet.
Using a proxy server is even easier when you work with web proxy services, which establish proxy connections directly in your browser. For greater flexibility, you can manually configure a proxy server in your browser or on your operating system. All that's needed is a proxy IP, which you can get from our free proxy list. Be sure to check out our setup walkthroughs for configuring a proxy on Windows, macOS, Android, and iOS.
While good, keep in mind that even though proxy servers hide your IP, they do not encrypt your traffic.
Tor Browser
Tor (short for The Onion Router) is a free browser designed for ensuring maximum online anonymity. When using it, data traffic is routed through a network of volunteer-operated nodes, known as Tor relays. Tor is based on the concept of asymmetric encryption, which provides your connection with multiple levels of protection (easily visualized as the layers of an onion).
With Tor Browser, you can anonymously surf the Web.
The main disadvantage to Tor is its strength. While great for security, its layers of encryption decrease speed. As such, you'll surf slower than with a (reliable) proxy server. In addition, Tor also has a poor reputation, since it's often used for dubious or illegal Darknet activities. But don't let these drawbacks discourage you from giving it a go - Tor is completely legitimate and legal to use.
Public WiFi
Should you want to briefly do a bit of anonymous online browsing, you can connect to a public WiFi network or hotspot. When doing so, you'll be assigned a new IP address. However, the dangers lurking on public WiFi definitely exceed those of other methods we've detailed here. This is because you're vulnerable to everyone else on the network. We strongly advise only visiting encrypted HTTPS websites on public WiFi.
VPNs
A virtual private network (VPN) is very similar to a proxy server: Your traffic is sent to an external server, masking your IP address. However, unlike a proxy server, a VPN also encrypts your data, which enhances your security. With a VPN, you'll be able to more confidently and safely connect to public WiFi, while enjoying all of the other advantages of IP masking, like getting around region restrictions.
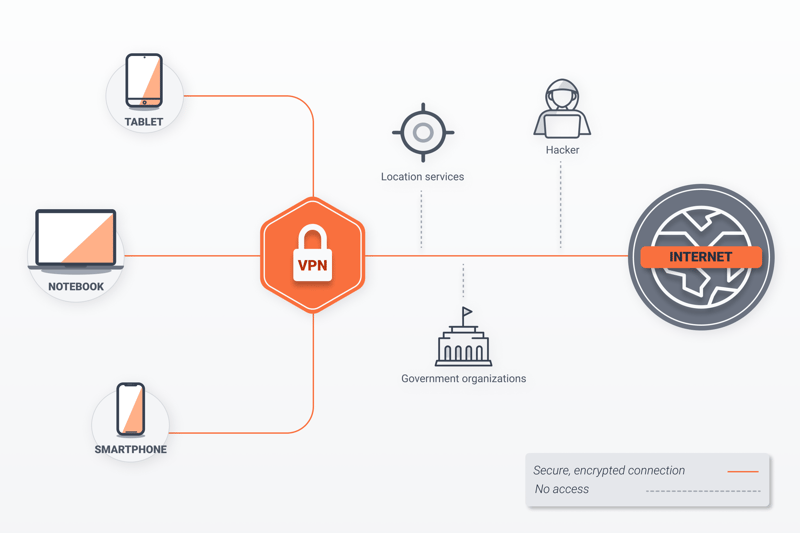
VPNs don't just hide your IP address, they also encrypt your connection.
In terms of user-friendliness, VPNs can't be beaten: Establishing a connection is simple and you'll only need a few clicks or taps to set up the VPN's client on your desktop or mobile device. And there are plenty of choices too, with both premium and freemium offers available. In our EXPERTE.com VPN test, we comprehensively reviewed 27 of the most popular services on the market.
Step: Block Tracking
Chances are good that whenever you're only, you're being tracked. Some of the solutions we've mentioned above, like VPNs, proxy servers, and Tor, do protect against this to varying degrees. However, there are other tools and methods that make following your online activities either difficult or impossible.
Browser-Based Methods
Most browsers offer integrated anti-tracking tools or features. These include:
Private Mode
Most browsers offer some sort of incognito mode, which hides traces of your surfing activity. This is primarily designed to prevent other users of the same computer or device from seeing which websites you've visited and doesn't really do much against industrial-scale tracking.Do Not Track
Several browsers, like Firefox and Chrome, come with built-in Do Not Track features. These automatically send requests from your browser to websites you visit, asking them to not track your activities. While better than nothing, websites are not obliged to consent to it.Tracking Protection
Some browsers take matters a step further. With Firefox, for example, you can guard against activity tracking by entering a command in the address bar.
In our anti-tracking guide, we'll show you how to configure these browser-based tools in Chrome and Firefox.
Browser Extensions
If your browser's tools aren't enough, you can take the fight to trackers by installing additional browser extensions. For example, Privacy Badger (Firefox, Chrome, Edge, and Opera) is free and either prevents known ad trackers from monitoring your surfing behavior or deactivates them completely.
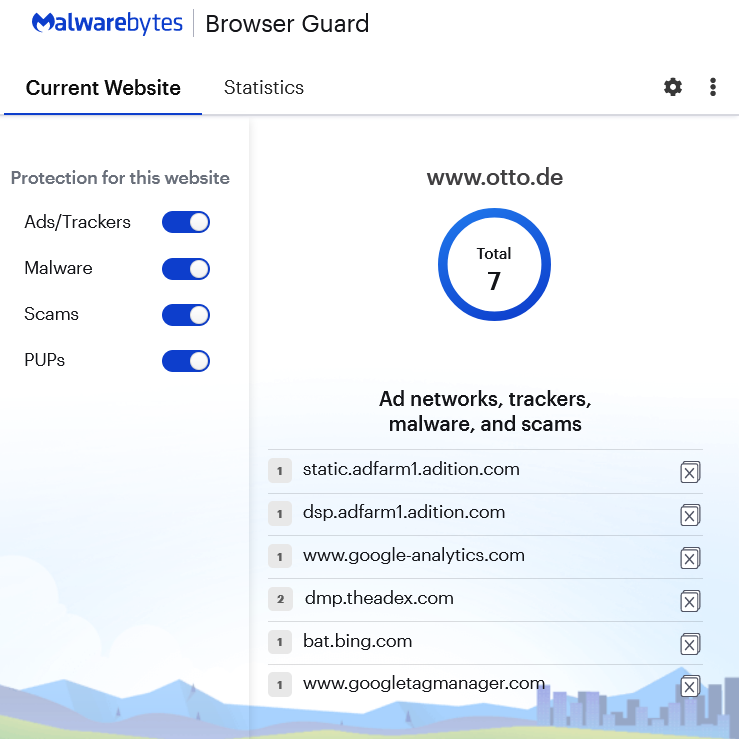
Browser Guard, from Malwarebytes, is a free browser extension that helps against tracking.
Browser Guard (Chrome, Firefox, Safari, and Edge) from the antivirus software developer Malwarebytes is a free browser extension that blocks trackers and ads. It also protects against malware and other unwanted downloads.
Privacy Browsers
There are also privacy browsers, which are even more focused on enhancing user anonymity. We already mentioned one of these above, Tor, but there are many other options to choose from too.
Data privacy is the centerpiece of Brave browser.
Brave is just such a free and open-source browser. Like Chrome, it's based on Chromium and offers plenty of security and privacy settings, while also blocking ad trackers and ads.
Anonymous Search Engines
Few search engines can compete with Google. However, high-quality search results come at a price and you pay it with your data. There are anonymous search engines like DuckDuckGo, Startpage, and Qwant. Of these, Startpage currently offers the best combination of privacy and search result quality.

Startpage is one of the most promising, privacy-focused alternatives to Google.
We've introduce some of the best alternatives to Google in our article on anonymous search engines.
Antivirus Software
Plenty of antivirus programs come with integrated anti-tracking capabilities and features. EXPERTE.com's top performer, Bitdefender automatically installs an anti-tracker in your browser. Keep in mind that some software does hide these features behind paywalls.
Antivirus programs, like Bitdefender, can also help against tracking.
Be sure to consult our EXPERTE.com comparison of the leading providers to learn more about the market's best antivirus programs.
VPN Guide: Surf Anonymously and Safely
VPNs offer one of the best all-in-one solutions for safe and anonymous surfing. Not only do they hide your IP address and location they can also help you get around country restrictions and censorship and encrypt your traffic. And the cherry on top? You won't need to manually configure these in your browser or on your system: Just install the app from the service you've selected.
To create a secure VPN connection, follow these steps:
Step 1: Decide on a VPN provider (feel free to consult our EXPERTE.com VPN comparison) and register on their website. For the following steps, we used NordVPN, our review's winner.
Step 2: Download your VPN's app. Most of the time, you can find apps for all operating systems and devices from the provider's website.
With NordVPN, all of the available apps can be found in your Nord account.
Step 3: Install and open the VPN app. You'll be able to connect to any of the VPN servers the provider lists.
Most VPN services operate servers around the world.
Step 4: Click on a server from the list or select a location from the map to create a VPN connection.
Tip: Problems with VPN connections can occasionally arise. To not unknowingly surf without a VPN connection, most programs come with an integrated kill switch, which automatically severs your Internet connection if the VPN is disrupted. After you've installed the VPN of your choice, double-check the settings to make sure that the kill switch is activated.
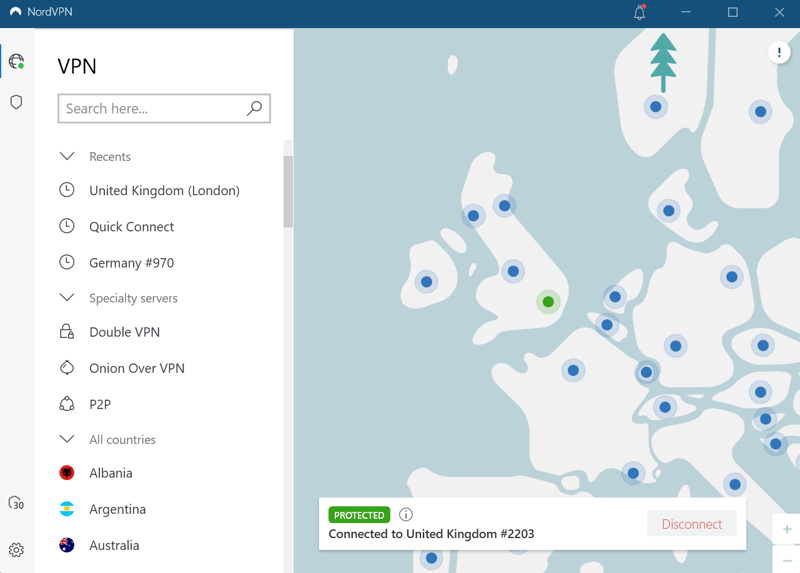
Now you'll surf with an encrypted VPN connection.
Each VPN app looks slightly different, however, the underlying principles are always the same. The only thing you have to worry about is finding the provider that best matches your needs.
The Best VPNs: Our Top 3
We assessed and compared 27 of the most popular VPN services according to their user-friendliness, features, and security (among other factors). Here are our Top 3:
NordVPN

NordVPN was best in class in our VPN comparison, since the Panama-based provider combines high-security standards with top performance and tons of features. In our VPN speed test, NordVPN also came in first, setting the bar for both downloads and uploads. The price-performance ratio is good, especially if you're ready to commit to a longer subscription.
ExpressVPN

ExpressVPN also performed excellently in our speed test, and its server network is even larger than NordVPN's. We found its apps to be user-friendly, and welcome the provider's commitment to independent security audits.
Less impressive was the service's price tag, as ExpressVPN's most affordable subscription costs three times as much as that of our top price-performance pick (for a monthly subscription, the difference is negligible). Another cause for concern: The provider is owned by Kape Technologies which in the past, was criticized for spreading malware.
Surfshark

EXPERTE.com's price-performance winner was Surfshark, which, in comparison to its competitors, is relatively new to the market. But don't let that fool you - it's among the best providers owing to its excellent performance, many features, and unbeatable subscription price (for 12 and 24-month contracts).
For more extensive reviews of these and the 24 other providers from our sample, be sure to consult our VPN comparison.
Conclusion
If you're using the Internet, you should know that total anonymity does not exist. Life is difficult to imagine without the Web since it makes many things possible or easier. At the same time, we pay for all of this convenience with our data. IP addresses and tracking (the monitoring of our digital activities) help companies, ISPs, and cybercriminals gather clues that let them know who the person is on the other side of the screen.
However, there are ways to make yourself more anonymous online. You can conceal your IP address with a VPN, proxy server, or Tor browser; or confound trackers with browser-based tools, special extensions, and antivirus software.
The best all-around method to enhance your online anonymity is a VPN. This won't only hide your IP address, but also encrypt your connection's traffic. To learn more about which security promises VPN services make, as well as the risks and limitations of these, be sure to read our article, VPN Security: Are VPNs Really Safe?
FAQs
There are many ways to improve your online anonymity. You can mask your IP address with a VPN, proxy server, or Tor browser. You can also block or prevent tracking by configuring settings in your browser, adding extensions, and/or using a privacy browser, anonymous search engines, and antivirus software.
Tor Browser offers the greatest degree of anonymity by asymmetrically encrypting your traffic. This is done by routing it through a network of nodes (relays), each of which adds another layer of security. However, alternatives also exist which come with advanced privacy settings, like Brave browser.
100% anonymity can never be guaranteed. With EXPERTE.com's privacy check, you can quickly see which traces you leave online.











