Two-Factor Authentication - How To Secure Your Accounts
All that stands between your riches, reputation, privacy, and sensitive data are a few letters, one or two numbers, and a symbol here or there – if at all. Passwords serve as our digital bodyguards and while important, it's also necessary to be able to easily remember them. How many of them have you typed in today?
Most people are logged in somewhere at all times. Convenience leads us to create easy-to-remember passwords or use the same ones over and over again. Who is actually able to remember a string of random upper- and lowercase letters, numbers, and special characters?
But here is where the dangers lurk. As a general rule, the easier it is for you to remember a password, the easier it is for a hacker to crack. Once that occurs, cybercriminals will have access to your most sensitive data. This applies in even greater measure to your password manager's master password.
Should you want to make hacking into your account nearly impossible, you're going to need two-factor authentication.
Two-factor authentication, or 2FA, gets its name from the addition of a second factor to your security. When logging in to an online account with 2FA, you'll need something that you know (i.e. your password) as well as something that you physically possess (such as a smartphone or signature).
As a result, even if your password winds up in the wrong hands, your online identity remains protected owing to the second form of verification.
How Does Two-Factor Authentication Work?
Once 2FA has been activated, simply log into your online account the same as you did in the past, using your username and password. Since passwords only provide limited protection, you'll need to verify your identity through an additional step. Often, this is accomplished by sending a PIN to a smartphone linked to that account or generated by a 2FA app.
The advantages of two-factor authentication are obvious:
Enhanced protection
Passwords are rendered useless to hackers and cybercriminals since they also need your smartphone or a printed list of TANs to access your data.You choose the technology
A number of different 2FA methods exist, as well as a wide selection of free apps for smartphones and tablets. This makes it possible to choose a provider that best fits you and your gadget portfolio.Increased productivity
2FA allows multiple users to access shared databases. Businesses can use that added flexibility to their advantage.
But that extra layer of protection is not without disadvantages:
You depend on the factors
There's no guarantee that your authentication factors are always available when you need them. If, for example, your smartphone has been damaged, stolen, or without any battery, you can't use 2FA.False sense of security
Let's assume you lose the second authentication factor. Now you're in the same situation as a hacker who wants to gain access to your account. If you can recover your online identity through some recovery feature, a skilled data thieve could do the same. So, stay vigilant, even when using 2FA.
With that said, the advantages of using 2FA far outweigh its disadvantages. However, not every 2FA method is the same. As we noted above, there exist numerous providers, methods, and applications, with the setup process varying from application to application.
The example below provides a step-by-step demonstration of how to set up two-factor authentication with one of the most popular password managers.
Example: Setting Up 2FA With Dashlane
Dashlane is one of the 12 tools we reviewed in our comprehensive analysis of password managers. Like many of its competitors, Dashlane offers users the ability to turn on 2FA, however, this must be done manually.
To start, go to the "Extras" submenu or press Ctrl+O to open the app's settings. Then go to "Security", and click on the "Two-Factor Authentication" tab.
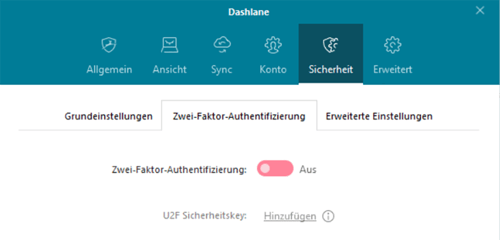
In the pop-up window that opens, you'll be able to select whether you want 2FA to be activated for every login or only when logging in from a new device. Choosing the former prevents thieves from gaining access to your account even if they have your master password and your devices.
In order to use 2FA with Dashlane, you'll need an authenticator app. This means that apart from knowing your master password, you'll also need to physically have a compatible smartphone or tablet with the app installed on it.
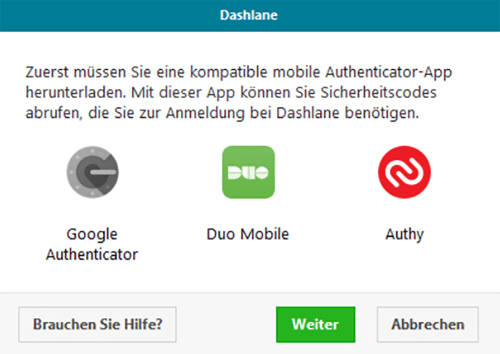
To do this, download a compatible app and follow its installation instructions. For our purposes, we used Google Authenticator. You can input the key provided by Dashlane or scan the QR code with the authenticator app.

And that's it! Your Dashlane app now has 2FA. Depending on your settings, the app will challenge your identity using the authenticator app you selected, either whenever you log in, or only when you do so from an unknown device.
Dashlane uses authenticator apps, however, there are other methods for applying 2FA:
• TAN/OTP systems (these also work with printed lists)
• Software or hardware tokens
• Biometric characteristics (fingerprint, retina scan, etc.)
What if I Lose My Device?
2FA is great but only if you physically possess the second authentication factor. Sometimes phones or tablets are stolen or lost. No worries though, as even in that scenario, password managers have got your back.
Returning to our example, Dashlane generates 10 backup codes when you configure two-factor authentication that you can save onto your hard drive.
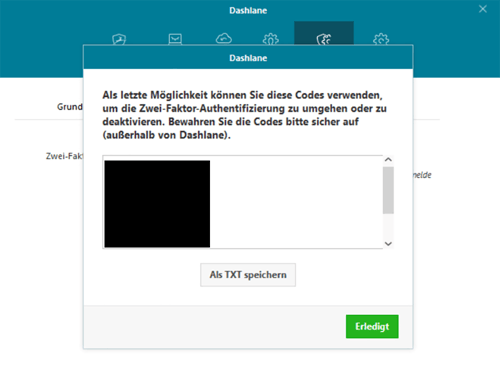
Each combination serves as a one-time replacement for the security code generated by the authenticator app. If you want to turn off 2FA or switch devices, you'll need to input one of those codes.
Like we mentioned above, there are many ways to use two-factor authentication and every password manager takes a unique approach. Some provide 2FA functionality to premium users only, so pay attention to this when selecting a service.
In general, 2FA is becoming more and more important to consumers with providers reacting to the increased demand by integrating it into their platforms and making it as easy to use as possible. For further information about password managers and what they can do, be sure to check out our guide.













