Whether for shopping, social media, or banking – we use the Internet for almost everything. Most of the time, we're less cautious online than we would be in real life. Cybercriminals know this and try to make the most of it by bullying, defrauding, or extorting anyone unfortunate enough to cross their path.
Below, we'll let you know what the seven biggest dangers online are as well as some practical countermeasures.
Below, you'll find the seven biggest dangers online, increasing in severity from tracking to malware and everything in between. For each, we'll briefly explain the threat as well as what steps you can take to counter them:
Tracking
Website owners, companies, or even criminals monitor your online activities using cookies as well as IP address and browser fingerprinting.Spam
Junk emails aren't just annoying, they can also open the door for malware to infect your system, or signal an attempt to gain access to your personal data.Data Leaks
Whenever an organization or website suffers a data leak, reams of personal data and passwords are suddenly made public. If you're a member or account holder, you instantly become vulnerable to cybercriminals.Doxing
Unfortunately, cyberbullying has grown in intensity and scale. Doxing is the malicious disclosure of personal or private information online, often in the hope that the victim will be targeted or harmed by others as a result.Identity Theft
Some digital criminals live very comfortable lives at the expense of their victims. Fraudsters misuse personal data like birthdays, addresses, and social security numbers to all sorts of devious ends.Phishing
Cybercriminals gain access to sensitive data through fake emails or websites. Thankfully, by exercising caution and using a few different tools, it's possible to protect against phishing.Malware
Malware and ransomware are, unfortunately, a big part of the Internet. With these, criminals are able to take advantage of security exploits in your browser or operating system, infecting your PC.
Tracking
Websites and services use tracking to follow visitor behavior and activity. On most reputable sites, you need to explicitly allow cookies that monitor your behavior. Most of the time, however, you won't be asked for your consent, or, you'll simply approve all of the options shown.
First-party cookies enable website owners to see what visitors click on and what they're interested in. Tracking content that originates from someone other than the site's owner is known as a third-party cookie. This is used to monitor user behavior occurring beyond that of the site itself, such as when a visitor clicks on an ad banner or plays a YouTube video.
Once the current browser session has ended, most cookies are deleted, however, some remain, keeping tabs on user behavior for a specific period of time, all the while gathering data. Such data is frequently used to personalize ads, however, telephone numbers, names, and other personal information can also be exploited by cybercriminals.
In addition to cookies and IP addresses, browser and device data are also collected in what is known as fingerprinting. Using the EXPERTE.com Privacy Check, you can see which digital footprints you're leaving online.
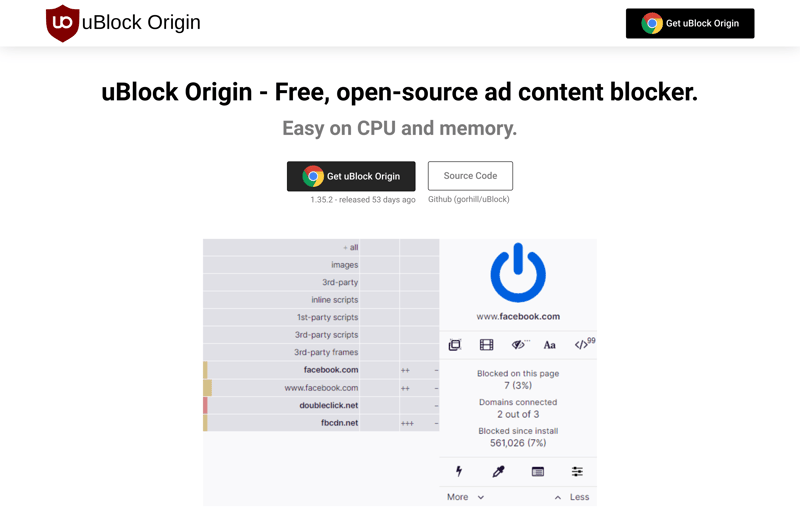
An adblocker can protect against tracking.
There are several ways to protect against cookie-based tracking: First, never mindlessly accept tracking when a pop-up requests your consent. Another prudent step is to log out from online banking, social media, or other websites when you've finished with them. Finally, you can use ad blockers to keep the most annoying cookies at arm's length. To see how effective these are against tracking, check out our comprehensive EXPERTE.com ad blocker test.
Unfortunately, deleting cookies and exercising care when using the Internet isn't enough to protect against the most persistent and dangerous types of tracking. For that, you'll need to conceal your identity with tools like proxies, Tor browser, or a VPN. Be sure to consult our guide to find out how to safely and anonymously surf the Internet.
Spam
The mass sending of unwanted and unsolicited emails is known as spam. In addition to email-based spam, there's also social media spam, SMS spam, and messenger spam.
Typically, spam advertises too-good-to-be-true financial products, romance, or wonder cures, like diet pills. Most of the time these are ads and never actually do what they claim to. Spam is annoying, clogs inboxes and requires the usage of a spam filter. In some cases, spam emails can even be dangerous, such as when they are concerned with phishing or spreading malware.
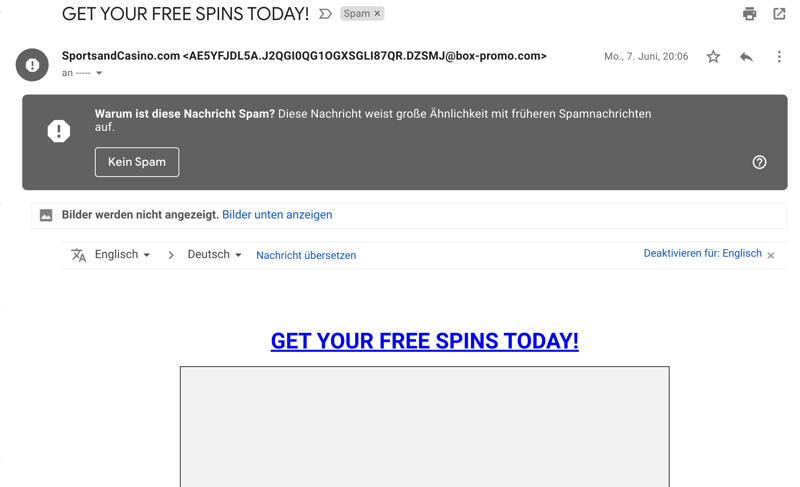
Most of the time (but not always), spam and phishing emails are easy to recognize.
Spam isn't always easy to recognize. If an email looks suspicious to you, check its sender and the message's content. Most of the time, spam emails advertise dubious products, using email addresses comprised of random numbers and letters. Often, the message's body or subject line will contain grammatical errors or have odd sentence structures.
Most email providers automatically filter spam messages to a separate folder. Should you receive a spam message in your actual inbox, mark it as spam, and the filter will "learn". To ensure that your inbox remains as spam-free as possible, use your primary email address only when signing up for reputable services. For browser games or contests, create a throwaway or secondary email address.
Sending spam is prohibited, and only companies that have received explicit permission to engage in advertising can send such messages. Should fraud or malicious activity be the true purpose, spam is even criminally prosecutable. Some websites sell lists of email addresses to spammers.
Even though it doesn't prevent spam, it's a good idea to keep your operating system and browser up-to-date and to make sure that the latest security updates are installed.
Data Leaks
Even if you've adopted the best security measures and carefully handle your personal data, it's extremely difficult to protect against all dangers lurking online. The most frustrating of these is without a doubt, data leaks or breaches.
Data leaks happen when personal data, passwords, and email addresses are stolen from an otherwise reputable site or service and published. Incompetence or a targeted cyberattack are usually the culprits. To see whether your email address has been compromised, we recommend Have I Been Pwned? You'll be able to check whether any accounts associated with your email address have been compromised.
Any information that goes public in the aftermath of a data leak is often used by criminals to gain access to user accounts or engage in identity theft. Stolen email addresses often become targets for spam campaigns and other unsolicited emails.
Sites like Have I Been Pwned? help to find out whether you've been impacted by any data leaks.
If your data has been compromised in a leak, change the passwords associated with those accounts as quickly as possible. Password managers make it easy to safely and conveniently manage sensitive data by automatically creating strong, unique passwords for each service you use. To find out which solution is best for you and your needs, have a look at our comprehensive EXPERTE.com password manager test.
For further information, we've also written an article on data leaks and countermeasures.
Doxing
From harmless digital pranks in the 1980s, doxing has mutated into one of the most troubling aspects of the Internet. Doxing refers to the undesired publication of private or sensitive data, such as personal addresses, telephone numbers, legal names, compromising pictures, or even fake claims of criminal activity. The goal is to silence or intimidate the victim, making it a kind of cyberbullying that is intended to do harm.
Some doxing attacks entail hacking in order to gain access to personal data, although less technically skilled evildoers will simply scour the web or social networks for personal information.
Doxers use social networks to collect personal and private information.
To make yourself as hard a target as possible keep your software up to date. This way, you'll be better protected against hacking. It's also advisable to be cautious when opening suspicious emails or messages, to regularly change your passwords, and to encrypt your hard drive.
Something else to keep in mind: Data that has been published online is difficult to remove. For that reason, be careful about what information you share online or with strangers.
We've prepared a comprehensive article with more information about doxing as well as what you can do to prevent it.
Identity Theft
Without warning, you receive an invoice for thousands of dollars from a website or company that you don't remember purchasing anything from. And you've never heard of any of the items or even seen them. You've likely been the latest victim of identity theft!
Identity theft has existed for a long time, but in its digital version, cybercriminals use personal data to make purchases online, or as a 'cover' for illegal activity. Typically, criminals manipulate personal data in one of two ways: Either to create fake social media or online shopping accounts or to co-opt your existing accounts by cracking your password. Both can have uncomfortable consequences and are criminally prosecuted.
As in most of the other threats we've discussed, strong passwords and up-to-date software are two of the best defenses against identity theft. Exercise extra caution when using public WiFi and encrypt your Internet traffic. Should you notice any suspicious activity, such as charges to your credit or debit card that you didn't make (even for small sums), contact your bank or credit card company.
In the event that you've already been the victim of identity theft, report it to the police. Tell your friends and acquaintances too since fraudsters will often attempt to co-opt networks of family members and friends to extract as many gains as possible. Dispute any charges that you didn't make and reach out to a lawyer or identity theft professional. You can find out more about identity theft and its consequences in our article on the subject.
Phishing
Phishing is the combination of "password" and "fishing", and refers to criminal activity aimed at acquiring passwords and personal data through fake websites, emails, or text messages. On many occasions, these look like legitimate communications from reputable companies, services, or banks, however, if you share your passwords or bank data, criminals will use the opportunity to ransack your account.
Spear-phishing and whaling are two specialized forms of phishing. The first targets specific victims, writing to them with well-researched messages, in order to improve the likelihood of success. Whaling, in turn, goes after the leadership of a company or organization in the hopes of eliciting large sums of money.
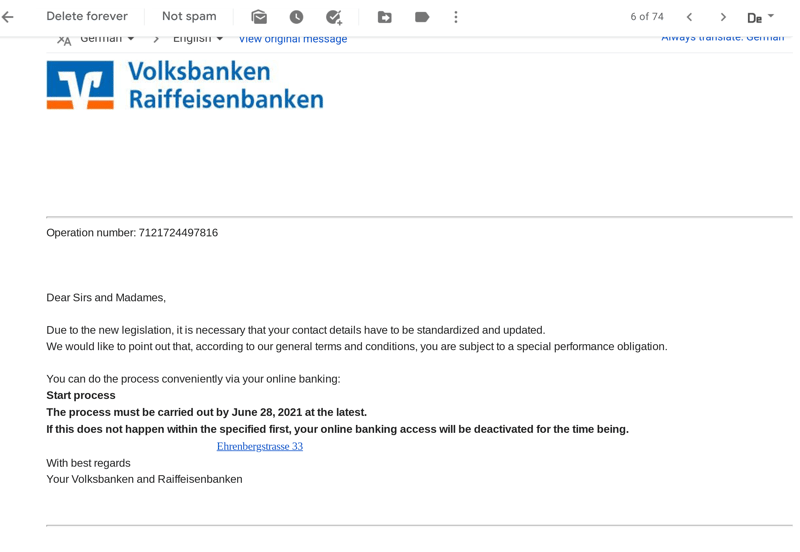
Phishing can vary in complexity and quality; the above message looks the part, but upon closer inspection, contains a number of errors.
As with all Internet-based threats, it's important to stay on your guard. For that reason, pay attention to the lack of a personalized address (i.e. "Dear Ms./Mrs." instead of "Dear Mrs. Smith"), grammatical or spelling mistakes, or suspicious attachments. Reputable companies and organizations will never ask you via email, SMS, social media, or telephone for your passwords or other sensitive data.
To reduce your vulnerability to phishing, we advise that you keep your software and drivers up to date. Modern browsers do a much better job of recognizing secure websites, and warning users when they are about to enter an untrustworthy one.
Malware
Whether a virus, Trojan, spyware, or ransomware, malware remains the most dangerous threat lurking on the Internet. Malware infects computers and unleashes chaos, with consequences ranging from performance issues to surveillance to outright data theft. Ransomware which forces its victims to pay for access to their files remains the most costly. Law enforcement and cybersecurity agencies recommend never paying up.
Our article on the subject offers a more detailed overview of the various kinds of malware that exist and what you can do against them.
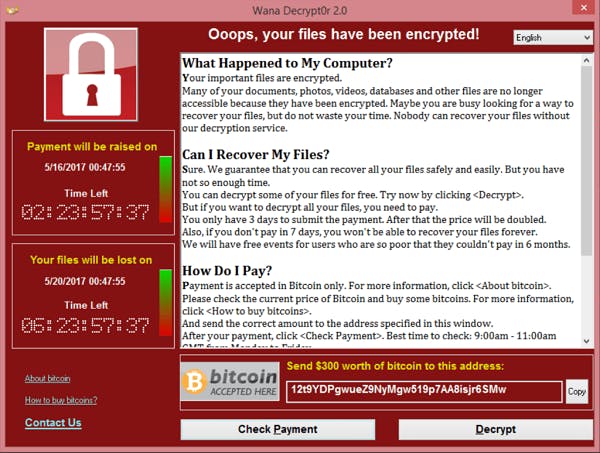
Ransomware is disturbing and shocking, with payment demanded in exchange for access to your files or data.
Should you suspect that your system is infected with malware, we recommend immediately taking countermeasures, since the longer such software is on your computer, the more damage it can do. To that end, we've put together a guide on how to efficiently and completely remove malware.
To prevent malware from getting onto your system in the first place, keep your software and drivers up to date, since security updates close exploits that viruses use to gain access to your system. Antivirus software is also a must, and to find out which best meets your needs (as well as what each has to offer) we recommend browsing our comprehensive review and comparison of 12 of the leading providers.
Conclusion
The Internet is a wonderful place, but not without dangers. Cybercriminals have grown skilled at gaining access to personal information, passwords, and banking data, so it's important to always be vigilant. Total security is not possible, since data leaks can lay bare even the most difficult passwords, or doxing can see your otherwise secure data hacked.
Nevertheless, with a mix of good judgment, common sense, up-to-date software and drivers, and, in some cases, antivirus solutions, it's possible to greatly reduce the likelihood of falling victim to such attacks. To that end, we recommend reading through our reviews of the leading IT security solutions and trying out our in-house tools. We're confident that these will strengthen your digital defenses!











