There are plenty of good reasons to surf the Internet anonymously. Concealing your digital identity can protect your sensitive data from hackers and help you bypass annoying region restrictions on Netflix or other streaming platforms. Online anonymity is even more important if you're a critical blogger or whistleblower who has to fear life and limb while handling sensitive information.
VPNs and Tor offer two popular solutions that promise enhanced anonymity on the net. Naturally, the question arises as to whether combining both methods increases your security even more? In this article, we'll explain when using a VPN in tandem with Tor can be beneficial, as well as how to effectively do this.
The Difference Between VPNs and Tor
VPNs and Tor offer two proven methods for protecting data and bypassing some online restrictions, such as geoblocking and censorship. They are, however, different technologies with distinct purposes, and come with advantages and disadvantages.
Here's a brief introduction to both solutions:
VPN — The Basics
With a virtual private network (VPN), all of your data traffic is encrypted. When you connect to a VPN server, you're assigned a new IP address which corresponds to that remote server's location. To outsiders, this makes it appear as though you're in the same region as the server—essentially giving you a different identity while surfing the net.
Thanks to user-friendly software for computers, smartphones, and other devices, VPNs are accessible to everyone—even beginners. No technical competence is required to set up a VPN connection.
With VPN clients, such as NordVPN's (shown above), you can establish a secure connection in seconds.
VPNs have a variety of uses. Among their greatest advantages are:
Protection while on public WiFi networks
Whether in a café, on a train, or at school, whenever you connect to a public WiFi network, you become exposed to risks. Hackers can easily steal your data and cause major problems. With a VPN, you'll be in safer hands, since all of your Internet traffic will be encrypted.Anonymous surfing
Internet service providers (ISPs) monetize the massive amount of data they collect from their users. If you live in the EU, you're protected by the General Data Protection Regulation (GDPR), however, in certain situations, your ISP will be legally compelled to share your data with government agencies. If you're connected to a VPN, your ISP could recognize that you're using a service but will be unable to associate you with your online activity. This means that you can anonymously surf the web.Bypass geo-blocks
Any website can track your IP address and determine the region you're in. Because a VPN allows you to use a foreign IP, your true location will not be discernible. As a result, you can easily bypass geoblocking and access websites and streaming content that would otherwise be unavailable.
Setting up a VPN is a breeze. Simply register with a provider of your choice, download their client, and connect to any server you like.
Here's an example of what it looks like with Proton VPN:
It's especially easy to create a VPN connection with services such as ProtonVPN.
VPN Pros and Cons
Faster than Tor
Shields all your online activity
Enables you to bypass geoblocking
Usually comes at a fee
Some VPN providers log your data
Tor — The Basics
Tor (short for "the onion router") also makes it possible to surf the Internet anonymously. Its peculiar name is derived from the multiple layers it encrypts your data in, resembling those of an onion.
Tor is an umbrella term for the entire program which consists of various components. Tor browser is based on Mozilla-Firefox and is preconfigured by the provider, so it's particularly easy to use with Tor's network, which consists of thousands of privately operated Tor servers.
One of Tor's unique features is its ability to access the darknet, the name given to part of the Internet that cannot be entered via the world wide web. The darknet contains plenty of legal content, however, it's often misused for criminal purposes such as drug or weapons trafficking.
You can use the world wide web as usual with Tor. However, there are a few differences, as some websites and services block Tor users out of principle. Should you use Tor via VPN (which we'll discuss below), you can get around these restrictions.
How Tor Protects Your Data
First, Tor browser downloads a list of available Tor servers. Using these, it plots a random route through Tor's network. Data is encrypted each step of the way until it returns to your computer, where it's decrypted.
This means that all information sent during this process is protected since each server (or step) only knows the IP address of the last and next server, preventing others from tracing where the data comes from and where it goes. The encryption also makes data analysis impossible.
On Tor Project's website, you can download Tor Browser for Windows, macOS, Linux, and Android in 32 or 64-bit versions. At the moment, the browser is available in 36 languages, with plans to add more.
You can easily download Tor browser on the Internet or clearnet.
If you have an IOS device, Onion Browser is a good option available in the App Store.
You can find more information about Tor and its browser in our article on anonymity online.
Tor Pros and Cons
Cost and ad-free
Conceals identity better than a VPN
Decentralized organization makes it extremely difficult to shut down the entire network.
Slow and ill-suited for video streaming or file sharing
Tied to Tor browser or other Tor applications
Doesn't anonymize all online traffic—only surfing
Combining a VPN and Tor
VPNs and Tor can be used together in several ways. Here are the two most common methods:
Tor via VPN
In this scenario, known as onion over VPN, or Tor over VPN, all data is first encrypted via VPN before it's sent through Tor's network.
Setup
1. Start your VPN client and connect to a remote server of your choice.
Tip: To achieve the best possible connection speed, choose a location near you.
Surfshark VPN connection to a remote server in New York.
2. Open Tor Browser. When Tor's network is up, you can use onion services and the darknet.
Tor browser's homepage.
Once such a connection has been established, your ISP will no longer be able to detect that you're using Tor. In addition, both your traffic and browsing behavior will be invisible. However, this method is only secure if you've selected a trustworthy VPN provider. EXPERTE.com's VPN comparison can help you make an informed decision.
NordVPN, the best-performing service from our sample*, offers a special onion over VPN feature, which allows you to quickly and easily combine the VPN connection and Tor's network. They adhere to a strict no-log policy and conform to high security standards overall.
VPN via Tor
In the VPN via Tor scenario, a VPN tunnel is created through Tor's network. This method is much more difficult to configure than Tor via VPN, and is only supported by a few VPN providers.
Here's how it works: The VPN service encrypts your data and sends it to Tor's network. After onion routing, your VPN server again receives the data from the exit node (i.e. the last link in Tor's chain), decrypts it, and sends it on to the destination server.
Setup
The setup for this method varies from provider to provider. We'll cover the steps using bolehvpn, a Malaysian VPN provider which supports VPN via Tor in a fairly straightforward way.
1. Start Tor browser, and then the bolehvpn client.
Bolehvpn client dashboard
2. Click on Proxy settings
Proxy settings in the bolehvpn client.
3. Click on Socks from Select Protocol Type. Input 127.0.0.1 for the Proxy Address and 9150 for the Proxy Port. Finally, click on the SAVE PROXY SETTINGS button to save your entries.
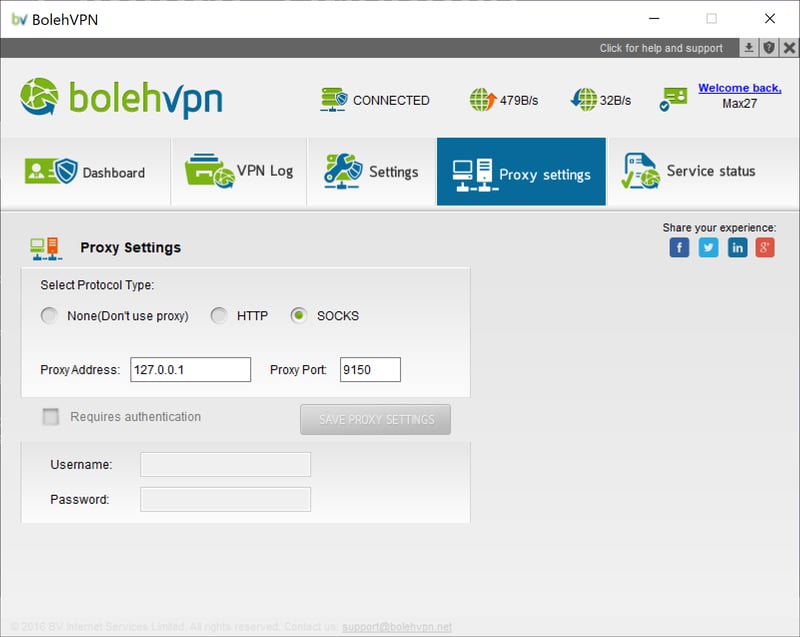
Proxy settings for VPN via Tor.
4. Start Tor. Once you've connected to Tor's network, navigate to the Dashboard tab in the bolehvpn client. Under Connect using, there's a drop-down menu. Select either FullyRouted-TCP or xCloakRouted-TCP from among the options shown.
5. Click the green Connect button to establish your VPN via Tor connection.
A VPN via Tor connection has been created with bolehvpn.
The provider notes that the speeds for such connections are rather slow. Should you be looking for an alternative to bolevpn, it's worth taking a look at AirVPN.
Comparison — Which Method Is Better?
Both methods enhance your security online, with little difference in terms of connection speed. Ultimately, it's up to you to decide who you prefer to trust with your true IP address—your VPN (Tor via VPN) or your ISP (VPN via Tor).
At EXPERTE.com, we recommend Tor via VPN because it works with any VPN provider and is very simple to use. In this scenario, your ISP won't be able to detect that you're using Tor, and the exit node of Tor's network is encrypted, offering additional protection.
VPN and Tor — A Match Made in Heaven?
Both VPNs and Tor offer powerful ways to enhance your security online. By combining the two, your data is afforded even greater protection. However, this extra layer of digital defense comes at the cost of your connection speed, potentially taking the joy out of streaming, file sharing, and even downloading.
If you're already a Tor user, spend a lot of time on the darknet, and don't care about bandwidth, you might want to consider the extra protection afforded by a good and reputable VPN provider. This will ensure that all of your Internet traffic is guarded as opposed to just your surfing behavior.
If you're particularly exposed to risks, for instance, as a regime critic, human rights activist, blogger, whistleblower, or journalist, then combining a VPN with Tor is highly recommended. This also applies to countries where Tor use is prohibited, such as Turkey or China.
However, if you have less at stake and only use the Internet for "normal" purposes, a reputable VPN will typically be more than enough. In our comprehensive EXPERTE.com VPN review, we compared 22 of the most popular services. NordVPN emerged on top thanks to its impressively high speeds, serious security, and an app packed with a number of great features.

Conclusion
If you're particularly security minded, combining Tor's network with a VPN connection can provide even more protection from hackers and other prying eyes. We recommend Tor via VPN, which works with any VPN provider. Our EXPERTE.com VPN comparison can help you choose which service best suits your needs.
It's important to be aware of the disadvantages inherent in using both VPN and Tor together; your connection speed will suffer, and even the best security solution has vulnerabilities. For example, the VPN service you've subscribed to could misuse your data or fall victim to hacking.
It's unlikely that a perfect digital security system will ever be developed. For that reason, it's essential to always exercise a healthy degree of caution online. To learn more about other useful IT security tools which help to reduce risk, be sure to check out our guides on EXPERTE.com.











