A weak password is like an unlocked door: It only keeps out the laziest intruders. Secure, unique passwords are the best protection for your online services. But what makes a password safe, and how can you keep track of different passwords?
We'll show you what a secure password looks like and how you can efficiently manage your passwords.
What Makes a Password Secure?
When it comes to passwords, the longer and more complex, the better. Here are some basic rules for creating good passwords:
At least 8 characters
Eight characters is the minimum length recommended by the National Institute of Standards and Technology (NIST). For Wi-Fi encryption, it should be at least 20 characters.Include upper and lowercase letters
Use a mix of uppercase and lowercase letters to increase complexity and make it harder to guess the password.Special characters
Include special characters like %, $, @, or & to make the password more random.No easily guessable terms
Avoid common words, names, or simple patterns. A secure password should not contain predictable terms or easily guessable sequences.
A secure password should ideally meet all these criteria. If you use a mix of special characters and uppercase and lowercase letters, your password can be shorter. Conversely, if you use a long passphrase, you don't need to include as many special characters.
What to Avoid?
On the flip side, there are some things to steer clear of when making a password. These include:
simple number and letter sequences and patterns like 12345, 77777, ABCDE, or asdfgh
family member or pet names
your birthdate
your phone number
other publicly accessible personal information
Unique Passwords for Every Service
One secure password isn't enough – you need many secure passwords. The reason: Even a secure password can fall into the wrong hands through no fault of your own, for example, through data breaches at companies that store your data.
If your password is exposed, every account that you use it with is at risk. Hackers can and do try to log in to multiple services with stolen credentials.
That's why it's important to use a unique password for each online account you have. This minimizes the risk that a single data breach will compromise your overall security. It may sound like a lot of work, but with a good password manager, it isn't too difficult (more on that later).
Password Checker and Password Generator
With EXPERTE.com's Password Checker, you can quickly determine how secure a password is. We'll tell you how long a computer would need to crack it and check if it's been involved in a past data breach.
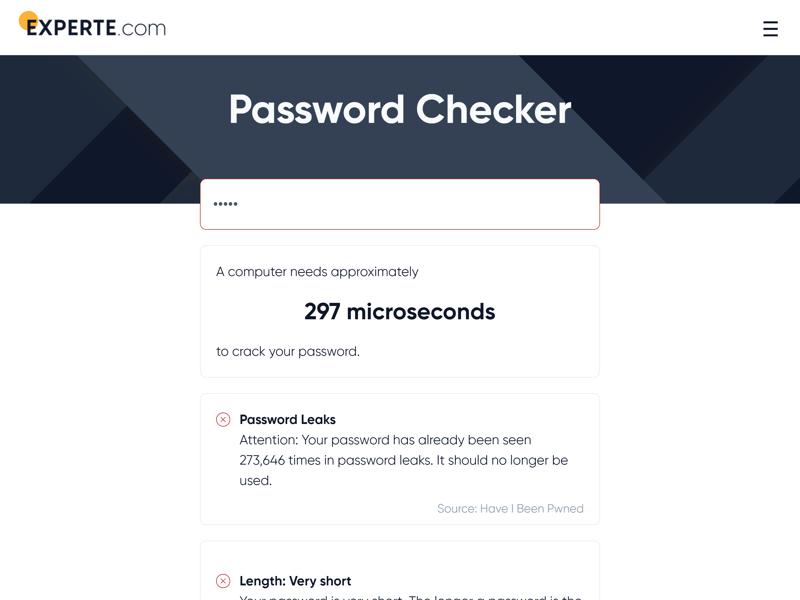
Check the security of your passwords.
You can also use our password generator to automatically create a secure password. It's possible to specify the length and types of characters you'd like to include.
A secure password might look like this: “8&uP$w!cQa#z”. An unsafe one would be “123456789” or “hello”. Oddly enough, the latter still manage to top lists of the most popular passwords in the US year after year.
Clearly, not everyone understands the importance of secure passwords. Laziness plays a big role: simple passwords are easy to remember. And creating a new password for each service seems like a lot of work – or is it? Not with the right tools.
Password Security Tools
Security and convenience can go hand in hand. Fortunately, there are tools and resources that make it easy to create and store safe passwords:
Password Managers: Easy Management for Multiple Passwords
A password manager is a program that stores your passwords (and other data) in a secure, digital vault. You can only access this vault with a master password. This master password is the only one you'll need to remember – the password manager handles the rest.
A good password manager:
automatically generates new passwords and saves them with login details
automatically fills in login details on websites
alerts you to potential security risks with your accounts
can also store other information, like bank details or passports
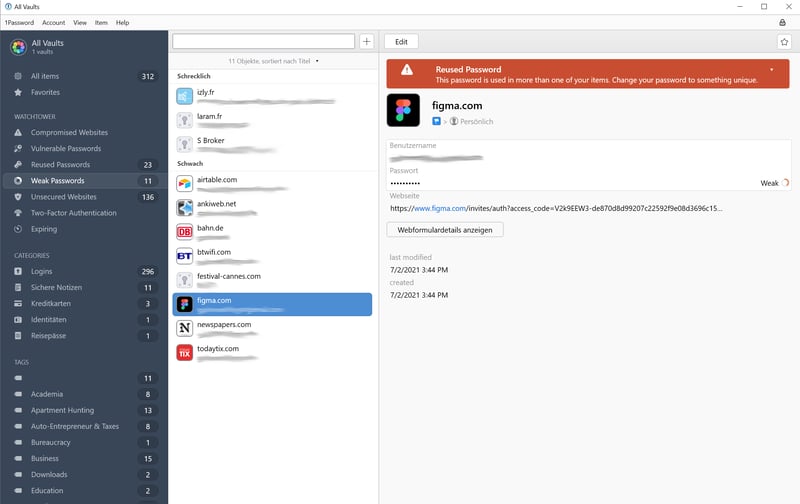
A password manager is a secure vault for your passwords.
Since every service today requires an account, it's nearly impossible to securely manage everything without a password manager. Even the NSIT recommends using one. But which is the best?
To help you choose the right password manager, we've thoroughly reviewed some of the most popular tools. You can find our reviews, along with many other guides and comparisons here:
Two-Factor Authentication (2FA)
Even the best passwords can't offer total protection if they fall into the wrong hands. This is where two-factor authentication (2FA) comes in. 2FA adds an extra layer of security by requiring a second verification factor in addition to your password.
Options for this second factor include:
confirmation in a smartphone app or via input of an SMS code
a code from an authentication app like Google Authenticator
a biometric factor like a fingerprint or facial recognition
a physical security key (e.g., YubiKey)
By enabling 2FA, you ensure that even if data thieves crack your password, they won't be able to easily access your account.
So make sure to enable 2FA wherever it's offered, especially for important services like online banking, email, and social networks. Many platforms now require 2FA. If you don't want to confirm your login every time you log in, you can configure 2FA to kick in when you log in from a new device.
Conclusion
A secure password is the best protection against digital intruders. It should be long, complex, and unique – don't use the same password for multiple accounts. The damage is much greater if one of your passwords falls into the wrong hands.
With a password manager, you can create unique passwords for every account you have and store them in a secure, digital vault. This not only protects you from identity theft but also makes managing your online identities much more convenient. Check out our password manager review to find the best program for your needs.












