The average Internet user has around 150 online accounts. That includes online banking, social networks, and email. At the same time, a whopping 81% of all reported data thefts can be traced back to a compromised or stolen password. FIDO2 promises safer and faster authentication without passwords. Below, we'll let you know how FIDO2 works and its advantages are.
What Is FIDO2?
FIDO2, or Fast Identity Online, is a password-less authentication method launched by the FIDO Alliance and the World Wide Web Consortiums (W3C). It's designed for mobile devices and browsers. Since it identifies users through verified hardware, there's no need to input a password.
Back in 2012, PayPal, Lenovo, Infineon, Nok Nok Labs, Validity Sensors, and Agnitio founded the FIDO Alliance to promote password-less online identification. The original members were soon joined by others, like Microsoft, Google, and Samsung. The second version of FIDO (FIDO2) was released in 2018. Its founders want the algorithm to remain open and non-proprietary, allowing it to be used on a wide scale.
Many apps and operating systems already utilize FIDO2, without their users being any the wiser. One example is the Hello login service on Microsoft Windows, which only requires the input of a numerical code. The correct PIN is saved locally on the computer and cannot be decoupled from it. Should cybercriminals crack the code, it won't help them, unless they have the computer too.
FIDO2's main characteristics are:
Authentication with external or integrated hardware keys as opposed to online password forms;
Two-factor authentication;
Asymmetric public/private key cryptography;
Locally stored authenticator
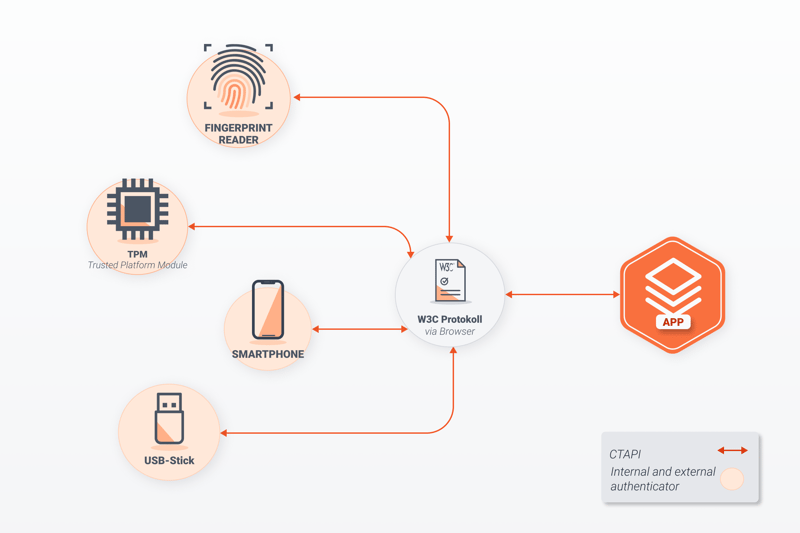
An overview of how FIDO2 works.
Hardware Keys
Instead of typing a password, FIDO2 users authenticate themselves with a trusted device, otherwise known as an authenticator. The connection between the authenticator and browser can be established via Bluetooth, USB, or NFC and includes:
USB sticks such as those from Yubico or SecureClick. These are known as FIDO2 sticks or FIDO2 tokens.
Smart cards like the WEGA 3DSA 2.0 acoustic card.
Trusted Platform Module (TPM) chips that are already embedded in most smartphones, laptops, and PCs.
Smartphones or laptops through which a fingerprint or PIN can be verified.
Two-Factor Authentication
More and more apps have started to utilize two, or multi-factor authentication. Users log in with their username and password but are then prompted to input an additional code, often sent by SMS. This method is very secure, however, it can be a hassle. If you don't have a good network connection, you might not receive the SMS before the code expires and won't be able to log in.
FIDO2's two-factor authentication relies on two independent components to legitimate a user, however, you won't need a second device since FIDO's hardware handles this. Instead, all that's necessary is the authenticator and an Internet connection. Some options include:
A complete, password-less solution, such as a smart card or TPM chip combined with biometric data or a PIN.
A username/password along with a token. In this case, FIDO2 enhances the security of standard password-based login processes.
Asymmetric Public/Private Key Cryptography
Traditional, password-based authentication methods are symmetric. This means that both the user and the website or service they want to access know the password. If the input password matches the one stored by the website, the user is legitimized. This method has a key weakness: A third party can hack the server where the password is stored, steal it, and input it just like the actual user.
In contrast, FIDO2 is based on asymmetric public/private key cryptography, which relies on a single pair of keys. The public key is publicly accessible (it isn't stored on the user's computer or device), while the private key is saved on the device in question. With each exchange, the sender encrypts data using the public key, however, to decrypt it, the recipient needs the private key. As such, the data cannot be accessed with only the public key.
How Does FIDO2 Work?
FIDO2 uses the FIDO Alliance's Client to Protocol (CTAP) and the W3C's WebAuthn-API. A CTAP integration facilitates connections between browsers and platforms through compatible devices (USBs, NFC, or Bluetooth). When the application (browser or app) connects to the authenticator, it sends a command. The authenticator reacts either with the requested data or an error.
The WebAuthn protocol, on the other hand, defines the interface that web applications use to integrate public/private key cryptography into a browser to enable authentication. This occurs when they communicate via CTAP protocol with the authenticator (TPM module or a USB stick).
Communication between the web server and end-user takes place across multiple steps:
- 1.
Users register on a website, submitting an email address and a PIN or fingerprint.
- 2.
The USB stick or TPM module creates a private and public key for the website.
- 3.
The web application saves the public key, while the private key is kept locally.
- 4.
When logging in, the web application sends a so-called "challenge request" to the device.
- 5.
The user unlocks the authenticator with their fingerprint or via PIN. As this step is voluntary with most authenticators, it's possible to configure a USB stick to unlock the authenticator once it's inserted into a laptop or computer. Of course, in this case, security is reduced.
- 6.
If the sent data is valid, the authenticator assigns a digital signature to the locally stored private key.
- 7.
The browser then sends the digital signature to the web application.
- 8.
Once the signature has been successfully verified, the end user is authenticated.
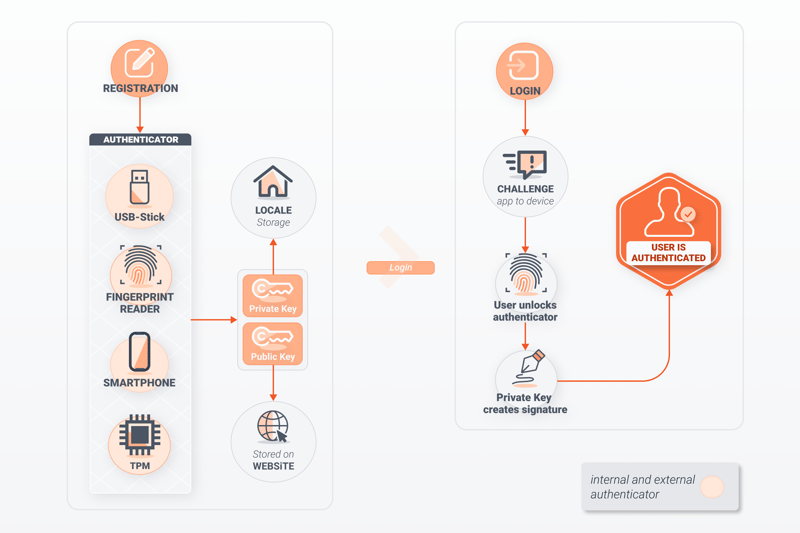
The FIDO2 login process.
How Can I Use FIDO2?
For verification to work, you'll need a browser that supports FIDO2. In addition, the web service or app that you intend to use FIDO2 with also needs to be compatible with the framework. Some examples of the latter include all Microsoft services (Outlook, OneDrive, Office, etc.) as well as a number of platforms, like Twitter, GitHub, and Dropbox.
When first logging in, it will be necessary to register. Here, it's possible to select the authentication method. Taking Windows Hello as an example, the first steps would be:
Go to Home > Settings > Accounts > Sign-in Options.
Click on Manage, and select the authenticator, choosing from Facial Recognition, Fingerprint Recognition, and PIN.
To add an extra security key, log in to your Microsoft account. Go to Security > Aditional Security Options.
Choose Add a new login or verification method.
Click on Use a security key and select the type of key (USB or NFC). After this, click on Next.
Input your key (i.e. insert your USB stick).
Create a PIN or type the PIN you've already created.
If necessary, touch the USB stick. This security measure verifies that a physical person is actually sitting at the PC or laptop.
Name your security key to identify it.
Sign in to Windows Hello with the security key.
How Secure Is FIDO2?
Public/private key cryptography is considered highly secure since it's nearly impossible to guess the private key. This has the added benefit of making FIDO2 more reliable than traditional, password-based authentication processes, in which hackers can easily determine weak passwords.
FIDO2 offers several other advantages as well:
Unique login credentials for each website.
The private key is only stored locally on your device, and not remotely, on a web server. This neutralizes the risk of phishing or data leaks.
Login data cannot be stolen by tracking user behavior online, since each pair of keys is unique to each website.
In contrast to password-based logins, it's possible for the same user to set and save multiple pairs of keys. This makes it possible to log in, even if one set of keys has been lost.
All the same, even FIDO2 doesn't offer total security. Should someone physically steal your FIDO2 stick and the accompanying device, they will be able to easily sign in. Since most people are more aware of their physical possessions than their digital ones, this is not difficult to protect against.
Should a user lose their authenticator, they can usually recover their account with a backup code or a second, pre-registered key. Of course, this varies from application to application. Websites that handle payment data typically have higher security standards than social networks do, for example.
Which Websites Support FIDO2?
To complete the FIDO2 authentication process, online services need to have the WebAuthn Web API. Both Windows 10 and Android (from 7.0 on) support this, as do the following browsers:
Google Chrome
Mozilla Firefox
Microsoft Edge
Apple Safari
Many popular websites and apps have also rolled out support for password-less authentication with FIDO2. These include:
Dropbox
Google Drive
OneDrive
PCloud
Google Wallet
YouTube
Gmail
Conclusion
FIDO2 offers a secure and relatively straightforward way to use apps and web services without a password. Thanks to its asymmetric cryptography, the private key remains local, providing extremely robust protection against password thieves.
Nearly all commonly-used browsers and operating systems support FIDO2, along with many web apps. To get started, all you need is a TPM chip, an external FIDO2 stick, a smart card, or any other software that can serve as an authenticator. In terms of authentication methods, both PINs and biometric data can be utilized. FIDO2 is a powerful and secure alternative to password-based logins for those tired of having to remember passwords.
On the other hand, if you aren't ready to make the jump to FIDO2 and would prefer to keep track of your existing passwords in a single place, we recommend checking out password managers. These conveniently and securely store your passwords for you and remember them so that you don't have to.












